Active Focus
Modern attackers are both persistent and opportunistic. They will be looking for ways into your environment, continuously hoping to pry on mistakes, vulnerabilities and other opportunities.
To combat this, we developed Active Focus.
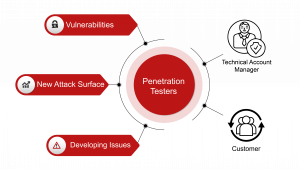
Active Focus is a comprehensive technology platform that features a variety of modules, including an Offensive Security Operating Centre. This combination of advanced technology and human oversight helps to ensure that our customers receive accurate and reliable information about vulnerabilities in their attack surface. By using Active Focus, our customers benefit from a robust and thorough approach to identify and address vulnerabilities before threat actors do.
What Active Focus Will Get You
The Solution
Traditional Penetration Testing is too slow. Cyber Criminals and other Threat Actors are rapidly running loops around our security teams. Security teams have a hard time prioritizing their time, understanding which risks need to be adressed, and what to fix, when and where!
This service challenges the existing methods of penetration testing and reactive security models, by defending forward. We are leaving our castle and the high walls we have built, and examining ourselves from the outside, in the perspective of a threat actor, finding holes and vulnerabilities before real attackers do. We call this Attack Surface Management and Always-On penetration testing.
Security organizations struggle with understanding how attackers operate, and how their organization becomes vulnerable over time. River Security is a razor sharp spear tip when it comes to offensive services, allowing us to provide our customers with relevant information on where security teams should prioritize.
We utilize ranges of Cyber Threat Intelligence, Penetration Testing techniques and much more to help ensure our customers can patch what is needed, when it is needed.

Our Customers Say It The Best
The team is very knowledgeable and has taught us a lot when it comes to proactive cyber security. They are agile and clearly has a lot of competence within their field, and we are happy to have them on our side in the ever-changing threat landscape.

One of the differentiating features of River Security is that they focus on real threats and areas that need attention – so we not only know about vulnerabilities, dark web disclosures and other issues, but also how they will affect our business.

...That’s where River Security comes in, offering their Active Focus service to keep us ahead of the curve with a constantly evolving attack surface, and even helping us to uncover the unknown...


How It Works
The Active Focus service is built on many components which enables our team to rapidly discover new attack surface, engage a team of penetration testeres and address risk as fast as posisble.
We developed a technology which gives us direct insights into what attackers see. When River Security's Offensive Security Operations Center receives an alert, it means an opportunity to attack our customer and help deal with immediate risks.
To achieve the necessary element of speed, correct information and actionability from our customers, we have developed a range of different modules that help us focus our attention at the right place, at the right time.
With the right people and the right technology, River Security is able to rapidly and effectively identify vulnerabilities and risk as they happen, in close to real time in many cases. It used to be the rabbit vs. the turtle, where the rabbit were the threat actors and the turtle was you and me, but we have finally taken back the advantage.
Explore How We Do It
Or see our page on how we fight cyber criminals
Steps To Better Security Hygiene
More About Our Service In These Selected Articles
Why We Monitor Technology
A key pillar in every organizationTECHNOLOGY Why and how do we monitor it? What kind of opportunities does it present our Offensive Security Operations Center? With aged technology comes vulnerabilities. These can in some cases, but far from every case, be exploited by attackers. Identifying technology as it dates, but also verifying if conditions are…
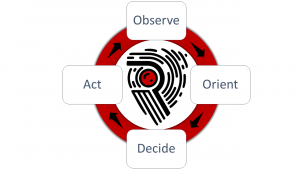
OODA Loops, Speed and Agility
To beat attackers at their own game, it is imperative River Security is able to more rapidly detect, uncover and find flaws in our customers environments than the threat actors. This process boils down to a process known as a OODA Loop. The OODA loops is a concept we have borrowed from the military. It…
Know Your Enemy
River Security follow closely the attackers’ behaviors and attack techniques. In studying attackers Tactics, Techniques and Procedures (TTP’s), our tools are sharpened and tailored to discover weaknesses in organizations defenses so we can better defend ourselves. Our Red Team uses the same attacks and techniques of attackers, and those we use in penetration tests, to…