
Ransomware Roulette – Level up or pay up
As we all know, at least to some extent, cryptocurrency solved the main problem (if we ask threat actors, that is) in ransomware and extortion attacks – getting away with the money. It became so easy to monetize the criminal act of breaking into organizations and encrypt their data that RAAS was born. What is RAAS you ask? Ransomware as a service. Not every malicious hacker has the time and ability to develop a robust ransomware attack, so they purchase one with the no-cure-no-pay guarantee.
This may translate into, although somewhat simplified; Any malicious hacker can singlehandedly mount a serious attack if he/she can find a hole in the target’s defenses. Armed with this knowledge we must realize that it is paramount that we step up our defensive capabilities.
Traditional security testing in form of penetration tests and the almost useless vulnerability scan gives a snapshot of the threat landscape, at best. Many companies schedule tests like this several times a year, either to check that box that satisfies some compliance or, hopefully, because they are starting to understand the threat.
This is certainly better than doing nothing, but it is essentially the same as protecting your herd of sheep 4 times a year. Quarterly you send the herder out to check that fences are satisfactory, but ONLY where you are aware there are fences, and ONLY the fence you believe is most important and ONLY a specific area of that fence you fear might be damaged.
The herder checks the parts of the fences in question and documents the current situation with a photo. This is a penetration test. It provides the company with a snapshot of the “status quo” at the exact time the herder inspected it. It will not reflect the hole that a farmer left for 2 weeks before he fixed it in a hurry the day before the inspection. Nor will it include the breach that will happen two weeks into the future due to the inadequate repair attempt prior to the inspection.
We need to powerup the penetration test, adapt it to maximize the value it yields. What if we upgrade the herder with a dog and send him to look at all the fences he can find and not just the ones you know of? Even better, what if we send him every single day? That would give him continuous control over existing fences, locations and build materials. And if there is a product recall, or otherwise a weakness in materials that is in use on a farm, he would report immediately.
Sometimes it feels like malicious hackers are ubiquitous, making the internet a hard place to be. It is never peaceful, always buzzing with attacks launching back and forth, left and right. Most times it is difficult to obtain any valuable information about the attackers. When anyone can part take in cyber warfare without being held accountable, attacks may never cease. The online war will never end, only change. In “The Art of War” Sun Tzu eloquently states:
“If you know neither the enemy nor yourself, you will succumb in every battle”.
Sun Tzu, The Art of War
We argue that this is especially true in cyberspace. After we map out their digital footprints, companies are time and again surprised to learn what they expose to the entire world. We cannot reference this, nor can we claim that this is a well-known fact, but in River Security, we have seen enough to label this lack of self-awareness (knowing thyself) de facto for a lot of businesses. This is only natural in a fast-moving world where digitalization is key to further increase profit. Through hacker eyes this is a growing attack surface.
By continuously monitoring client assets and online resources they expose, intentionally or not, we proactively tighten attack surfaces and reduce risks for companies in the long run. It should be obvious that this is not feasible nor entirely possible to do fully automated. River Security combine the best of two worlds, arming hungry ethical hackers with the best tools in automation to discover vectors, map resources, understand synergies, define targets, and attack them respectfully. This is as close to a real-world scenario as any simulation will get.
Better to have dogs on the inside of a fence collecting and controlling the sheep as soon as a vulnerability exist, instead of on the day of shearing, you find wolves holding your livestock at gunpoint, demanding ransom. That last situation is bound to escalate beyond PG-13 rating very fast.
Having tentacles into different areas of what people see as the internet give us the perceptive abilities required for a cybersecurity company. We are on top of the latest tactics, techniques, and procedures (TTP) deployed by threat actors. We are informed ASAP of new leaks and database breaches, always checking clients and their employees for compromises.
Having control over own composition and exposure is imperative. Adapting a proactive approach is highly preferable, if not the only valid approach. If you find yourself doing incident response, you are already losing. Sadly, many companies believe that purchasing the latest technology and deploying it on the network is a proactive approach. Intrusion Prevention Systems (IPS) and Security Information and Event Management (SIEM) serves a purpose, but they are not actively looking for vulnerabilities. One might argue they are not active at all. Every event the software produce is the product of a reaction to an initial action outside of the IDS/SIEM thus making it, by definition, a response.
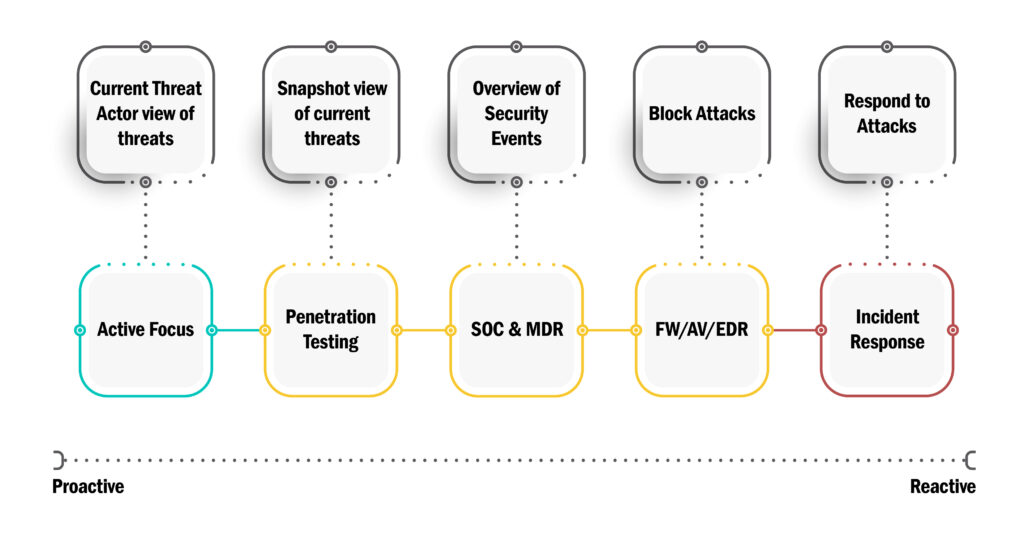
True proactivity here is the unprovoked action of actively finding your vulnerabilities before any threat actor does. This is what we do. By providing Active Focus to our clients, we are vastly reducing their risk of being breached. We continuously monitor the size of our clients’ footprints and the depth of the impression left exposed to the internet. We challenge any change in the perimeter and maintain frequent communication with the clients’ teams.
Do you have total control over company assets? Where they are and what protection mechanisms controls access to them? We know that many do not. Watch over your sheep, wolves attack when no one is around; keep your fence maintained at all times! Thank you for reading.


