Enhanced Security Posture
Identify and address vulnerabilities to enhance overall security.
Effective Risk Mitigation
Prioritize and mitigate potential risks with targeted measures.
Regulatory Compliance
Demonstrate adherence to industry regulations and standards.
Peace of Mind
Proactively protect assets and sensitive data for worry-free operations.
What does a penetration test conclude?
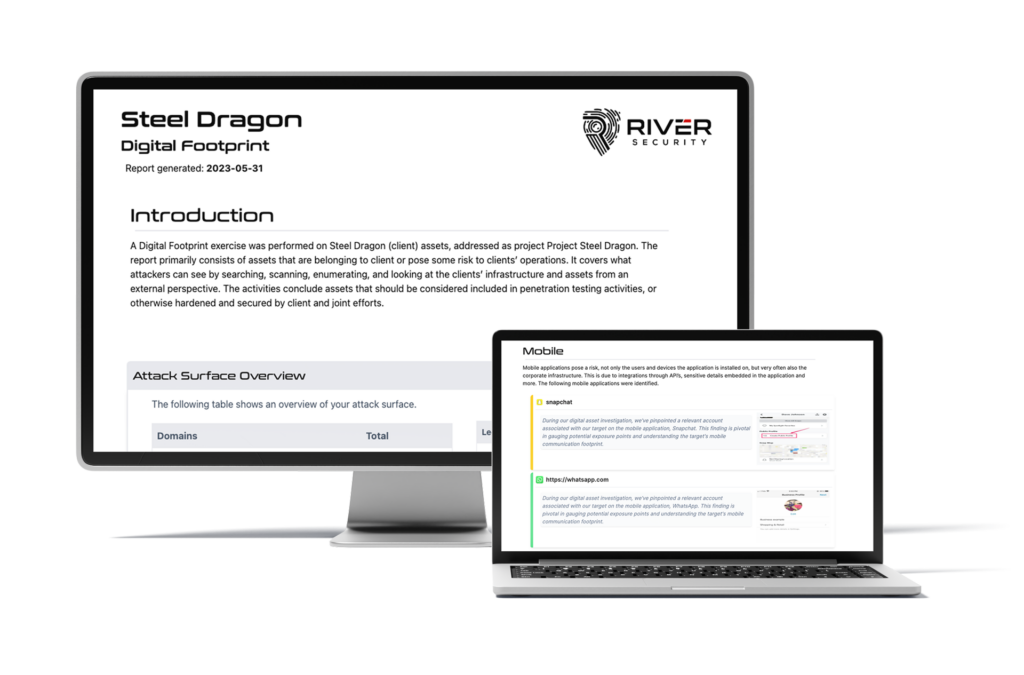
The testing will result in a report with actionable advise of what risk is currently exposed in the application. The report you receive will contain an executive summary describing the risks involved and recommended short- and long-term actions.
River also provide a full colour coded and prioritized list of vulnerabilities identified. Each vulnerability will be rated based on several aspects, e.g. the impact on confidentiality, availability and integrity. The vulnerability will also have a score impacted by things such as if the vulnerability is exploitable without authentication, from the Internet or not, and so on.
Each vulnerability contains a description on how it was exploited, demonstrating the appropriate risk, and also suggestions on remediation, both short- and long-term where applicable.
Our Customers Say It The Best



The team is very knowledgeable and has taught us a lot when it comes to proactive cyber security. They are agile and clearly has a lot of competence within their field, and we are happy to have them on our side in the ever-changing threat landscape.

Terje Einar Hunvik
Mesta
One of the differentiating features of River Security is that they focus on real threats and areas that need attention – so we not only know about vulnerabilities, dark web disclosures and other issues, but also how they will affect our business.

Ole-Martin Bækkeli
Azets
...That’s where River Security comes in, offering their Active Focus service to keep us ahead of the curve with a constantly evolving attack surface, and even helping us to uncover the unknown...

Arvid Eriksen
Sparebanken Vest
More about our service in these selected articles
Pentesting is Transforming: 8 Steps to a Successful Pentest Operation in 2025!
Pentesting isn’t what it used to be, folks. Gone are the days of single checklist exercises and surface-level scans. In 2025, we’re transforming the way we think about pentesting—making it a dynamic, intelligence-driven, and collaborative practice that does more than just “find vulnerabilities.” We’re taking a proactive, adversary-informed approach that considers not only what’s in…
The Art of Discovery: A Penetration Tester’s Journey Through a Django Misconfiguration
[Editors Note: Eirik Valle Kjellby is an amazing gentleman and the latest, as of October 2024, addition to the ever growing penetration testing team at River Security. He continues to amaze me in his hunt for vulnerabilities as part of our continuous and always-on penetration testing efforts. In this article, Eirik shares with us one…
Compliance and Confusion – Your Guide to Navigate the Most Common Frameworks and Regulations for Cyber Security
In this comprehensive guide I will go through the most common frameworks and regulations for Cyber Security, as there might be some confusion in how to apply them to the everyday work. The frameworks and regulations we will map out here are in the table of contents below. Use the links to navigate the article.…