Users and Cyber Threat Intelligence
Cyber Criminals Can Do It, So Can We! Is there any new opportunities Cyber Threat Intelligence provide our Offensive Engineers?

On a regular basis, organizations are compromised because of credentials of their users allow attackers an easy way into the organization, often via techniques such as Credential Stuffing and Password Spraying. It is imperative that, as a company which provides Offensive Services, we act as close to what other Threat Actors are doing. Such Threat Actors include:
- Script Kiddies
- Cyber Criminals
- Nation States
Simple techniques allow attackers on the inside of organizations, River Security need to act the same.
Credential Stuffing
Hacking does not have to be complex or hard and credential stuffing proves that point. It is a technique where Threat Actors are using leaked credentials from other domains, website and systems to break into yours. Fact of the matter is, unfortunately, many of our users use the same passwords, and often company email addresses, to register for third party systems. When these third parties are hacked, River Security tries to procure the credentials, like Threat Actors do, and re-use the credentials across your infrastructure. This is called Credential Stuffing.
Credential Stuffing allows the abuse of credential re-use and is a very common attack technique. River Security buys and collects Cyber Threat Intelligence from multiple sources to ensure we can stay on top of this issue on behalf of our customers. We also receive passwords from malware infected machines, often from machines originating from our customers user base, that allow us to protect not only the customers organization credentials, but often their clients too.
Password Spraying
Using lists of usernames and potential passwords, attackers will simply target different logins, for example email logins, Software-as-a-Service providers, Virtual Private Network concentrates and much more with automated software, allowing them to see if there is any accounts with weak passwords. It is called Password Spraying because they are essentially using large lists of potential usernames with a selected and crafted list of potential passwords. This kind of activity can go on for long durations of time.
Using all our available attack surface for a customer organization, River Security will attempt to spray specially crafted lists of passwords across the userbase. If at any moment in time our attempts are successful, contrary to a cyber criminal, we will immediately notify the customer about our success.
Procuring Cyber Threat Intelligence
Procuring, producing and consuming intelligence regarding the latest attack vectors, credentials and the current status quo is of the essence for an offensive team. River Security, through networks of partners and through our own investigative efforts, procure this intelligence and use it in our offensive operations.
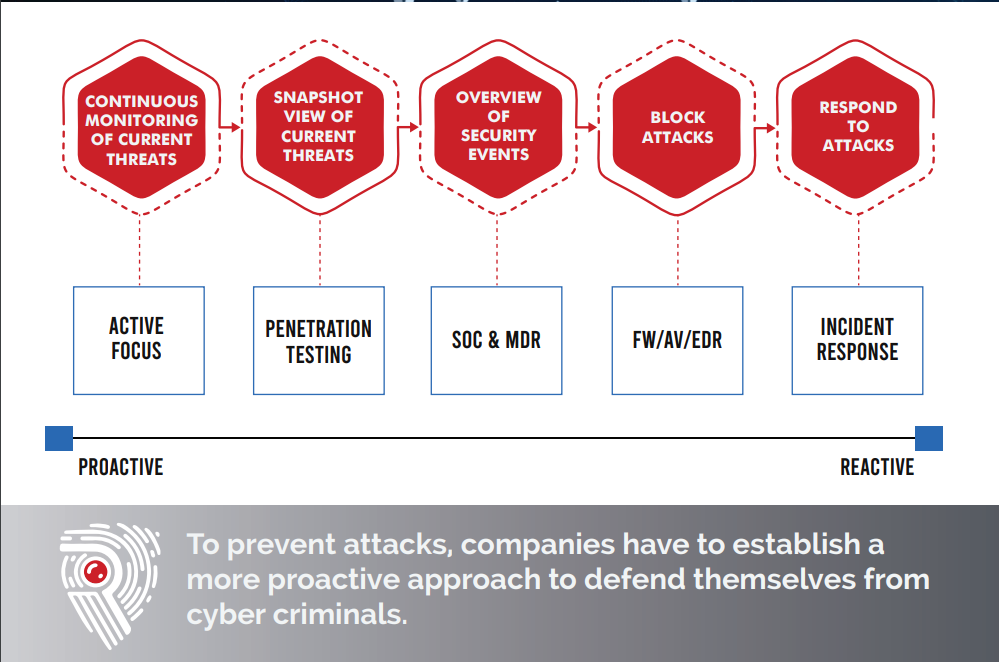
While every penetration test will attempt to utilize the latest and current Threat Intelligence, the fact we are doing a continuous always-on assessment helps customers on a much pro-active basis. For many customers, consuming and turning Cyber Threat Intelligence into actionable value is a challenging task, but for Offensive Engineers it is second nature.
Applying Credentials and Breach Data as Part of Continuous Offensive Security Operations
River Security get a hold of employee credentials, which we apply as part of our credential stuffing processes, but there is more… Logs and data from malware, so called stealer logs, are also a part of our Offensive Team’s aresenal of tools. From malware logs we receive credentials, sessions and more, from infected computer systems. We look for data pointing to our customers computer systems and find credentials from password managers, sessions from browsers and passwords from forms, all posing a risk for our customers and the victims using our customers services.
