Why Do We Monitor for Domains? Finding Keys to the Kingdom!
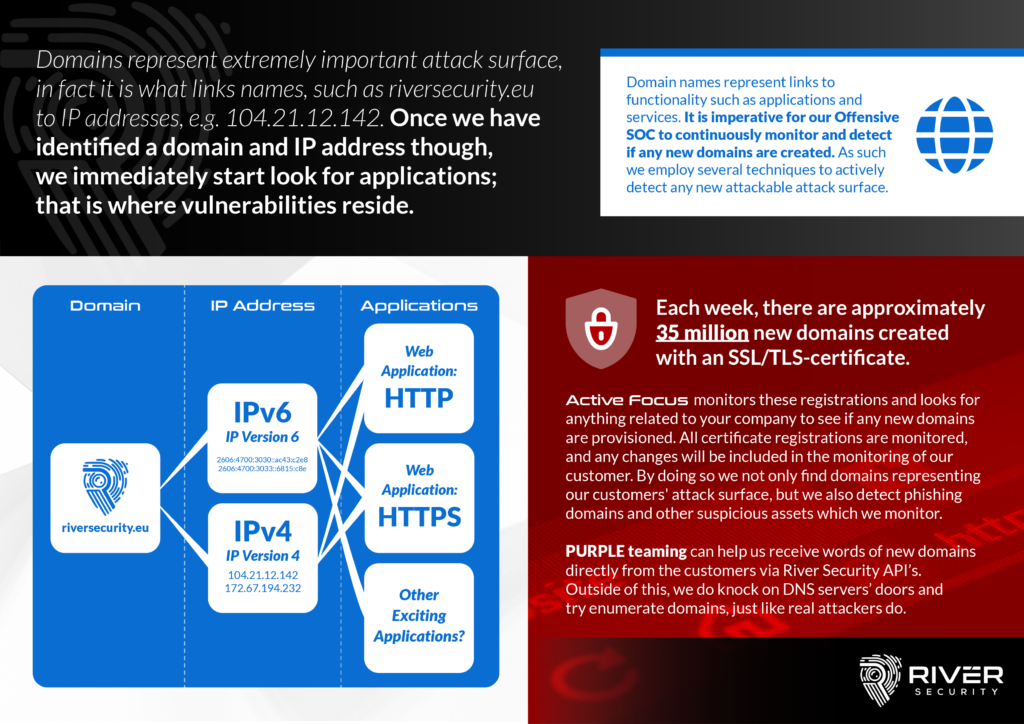
Domains represent a crucial and vital part of the attack surface our organizations expose. A DNS (“Domain Name System”) is a central part of every organization and can essentially be considered as a directory of all things accessible, pointing our computer systems to which IP address responsible for serving up functionality, applications and support to our users and customers.
Attackers consider domains and DNS as a treasure trove of information. What do YOU have that THEY might find interesting to attack? Our threat actors often look for what we, in River Security, call the path least travelled. You know, those systems nobody else has found, which our organization might have forgotten about, that are without governance, patch management and other security controls.
DNS contain a directory of what companies seek to offer their users and customers, River Security tries their best to always stay on top of what your directory holds. What new systems do you provision? What old systems can we find references too? All in all with the goal of continuously stay on top of the attack service and provide offensive services, as fast and accurately as possible, to wherever risk might surface.
DNS Points to Resources – Resources Hold Value
The DNS Value Chain for attackers looke like this:
- DNS Names are found
- Names Resolve to IP Adresses, IPv4 or IPv6
- IP Addresses may have opening in the firewall, exposing network services hosted on TCP and UDP
- These network services have applications, which may have vulnerabilties and value for attackers.
This is attack surface of which must be assessed by offensive security engineers to ensure risk can be uncovered and addressed before threat actors can.
It is all about proactively, from an offensive and penetration testing point of view, be able to quickly assess our customers new and existing attack surface. A pro-active and agile approach to security. This continuous approach to penetration testing is truly the bleeding edge of how traditional penetration testing is evolving into a new and better format.
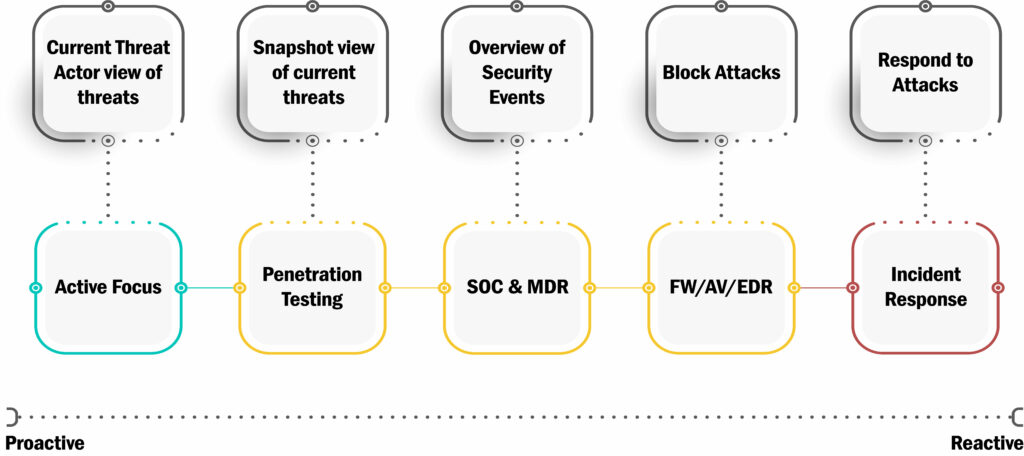
We use many techniques to ensure we get one step ahead of our threat actors, some in cooperation with our customer where they essentially notify River Security about the latest development.
Discovering, Assessing and Reporting on Vulnerabilities
There are multiple ways of discovering interesting domain names to attack. The most common way is to brute-force DNS servers using wordlists containing interesting names. For example, imagine we ask the DNS server for all things related River Security, we could walk through a list of possible names like this:
- Do you have customer1.riversecurity.eu?
- What about admin.riversecurity.eu?
- Anything at ftp or sftp.riversecurity.eu?
These questions are automated and range in tens of thousands to millions in certain cases; attackers looking for anything pointing to IP addresses they can then proceed to scan and attack.
CT Logs – Certificate Transparency
An extremely useful area for getting real time domain data on a customer is from Certificate Transparency Logs. These logs are updated in real time by Certificate Authorities and contain all the names of certificates representing your organization. River Security monitor these logs in real-time, but we don’t just look for your domains, we look for your brand. Instead of looking for say riversecurity.eu, we look for riversecurity. This enables us to find a lot more information than just what we know the customer manages, for example we are able to often find phishing domains and shadow IT. Identifying phishing domains in such an early stage of the attackers kill chain allows us to proactively block them in the firewall, kicking the legs of from underneath the attackers before they even got their attacks launched! Proactivity for the win!
