The Key to Successful Third-Party Management in the SaaS Space
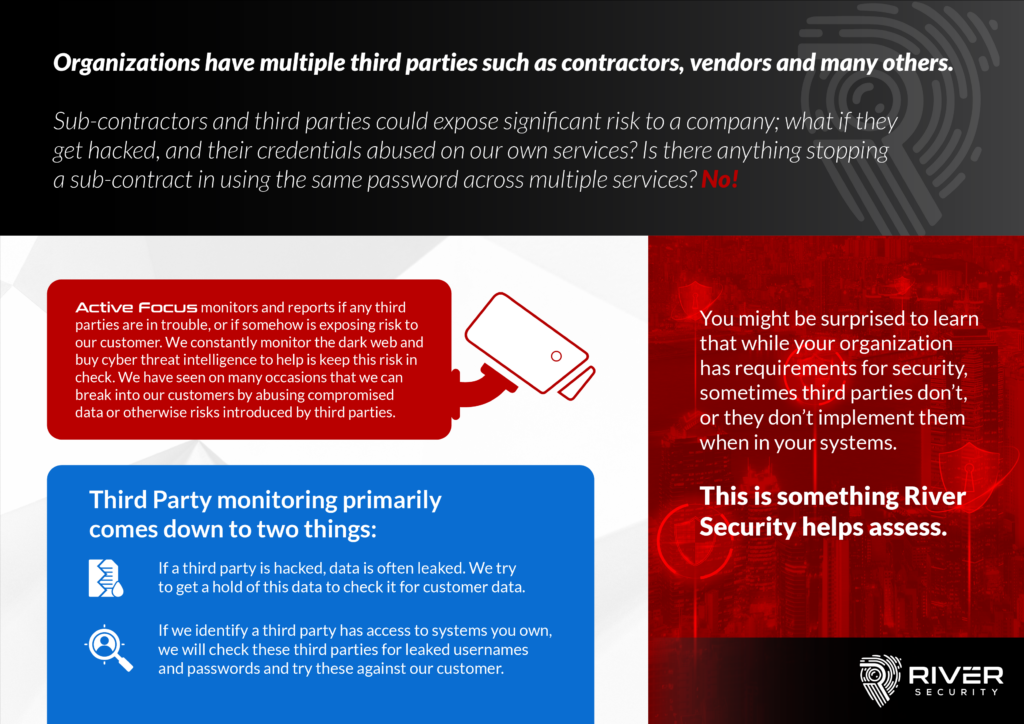
Third party vendors and subcontractors can introduce significant risk to a company, particularly if they are not properly monitored and managed. In order to help mitigate these risks, companies can take a number of steps to monitor and maintain an overview of their third party vendors. A major concern for many companies is that sensitive and proprietary data will leak, if and when one of their third-party vendors are breached.
One key step is to have clear, written contracts in place with all third party vendors and subcontractors. These contracts should outline the specific services that the vendor will provide, as well as any security requirements that the vendor must follow. This can help to ensure that the vendor is aware of the company’s security expectations and can help to prevent potential security breaches.

Additionally, companies can conduct regular audits and assessments of their third party vendors. These audits can help to identify any potential security vulnerabilities or areas for improvement, and can help the company to ensure that the vendor is following the necessary security protocols. River Security regularly supports customers in assessing their third party vendors.
Another important step that companies can take is to require all third party vendors and subcontractors to use unique, strong passwords for any accounts or services that they access on behalf of the company. This can help to prevent password reuse, which is one of the most common causes of security breaches. Companies can also require the use of two-factor authentication, which provides an additional layer of security by requiring the vendor to provide a second form of verification (such as a one-time code sent to a mobile phone) in order to access the company’s services.
Overall, monitoring and maintaining an overview of third party vendors is essential for companies that want to minimize their risk of security breaches. By implementing clear contracts, conducting regular audits, and requiring the use of strong passwords and two-factor authentication, companies can help to ensure that their third party vendors are meeting their security obligations and protecting the company’s sensitive data.

Where does Active Focus help?
With Active Focus, we closely monitor third parties to ensure they are not putting our customers at risk. We obtain, gather and collect data from CTI (“Cyber Threat Intelligence”) vendors who regularly scan the dark web, provide us with information and help us to stay informed about potential threats.
In the past, we have seen instances where our customers were exposed to risks due to compromised data or other vulnerabilities introduced by third parties. As an example we have on multiple occasions seen third-party accounts in our customer systems, where the accounts have had weak or leaked passwords, allowing us easy entry.
In the event that a third-party is compromised, River Security does its best to quickly get a hold of the information and vet it. We use a range of different procedures to help quickly comb through the data to find information which may put our customer at risk.
To address this issue, we recommend sharing the list of providers you use with River Security. This way, we can combine our monitoring efforts and work together to improve security.
Third Party Management and Attack Surface Management
Because of the nature of Attack Surface Management, River Security collects a wide variety of data, including data pertaining IP addresses, ownership data, email configurations and more. This enables River Security to understand a great deal about third parties our customers rely upon, allowing our customers a better understanding of third party management.
