Posts by
Chris Dale
Don’t Overlook Social Media Security: Protecting Your Brand
Social media has emerged as a significant yet often overlooked part of the attack surface for many businesses. Understanding where your brand is exposed online is crucial to safeguarding these...
Code Repositories: A Wealth of Information and Potential Threats. How River Security Protects Your Assets
At River Security, one of our key priorities is helping our customers protect their assets and data from potential threats. One way we do this is by identifying customer-owned code...
Cheating the Threat Actors: How River Security Monitors Cloud Assets to Stay Ahead
At River Security, we understand the importance of monitoring cloud assets in order to protect our customers from potential threats. That's why we have developed a unique approach to monitoring...
Mobile Apps Can Reveal Valuable Information for Attackers
Mobile applications have become a crucial part of modern business operations, with many companies relying on them to connect with customers, manage internal processes, and handle sensitive information. However, the...
Active Trace – Adding Deception to Aid Detection and Attack Surface Management
As the prevalence of cyber attacks continues to rise, it's more important than ever for organizations to protect themselves online. One tool that can help with this is Active Trace,...
Combating Digital Threats with Active Focus – Your Brand
Active Focus is designed to constantly monitor the digital attack surface of a business or organization, looking for signs of malicious activity or attempts to fraudulently use the company's brand....
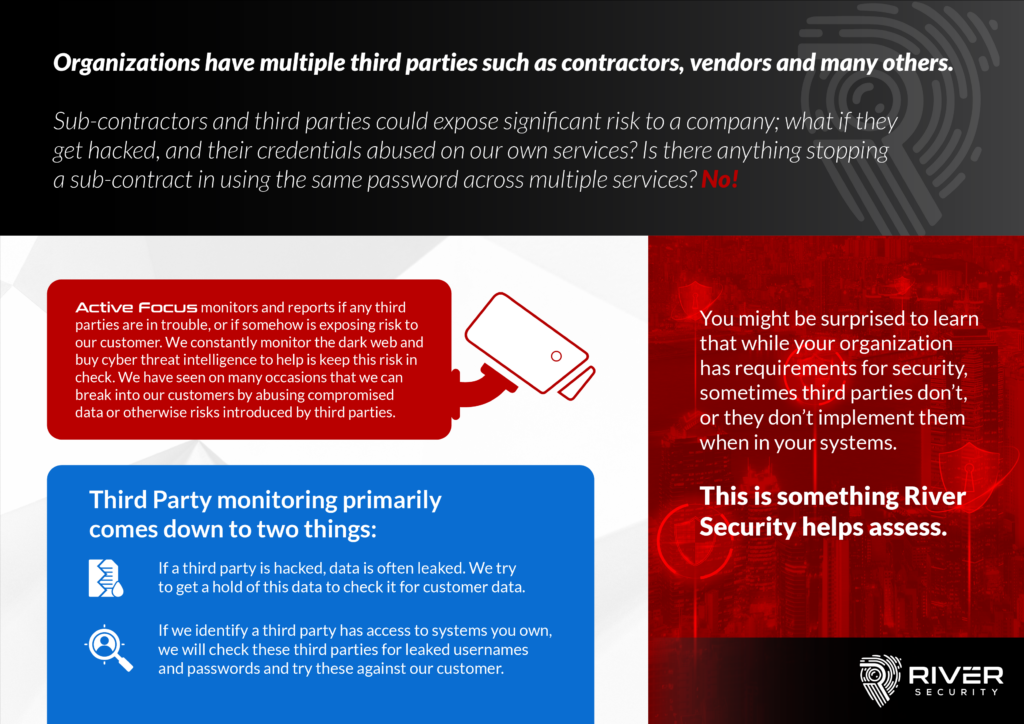
The Key to Successful Third-Party Management in the SaaS Space
Third party vendors and subcontractors can introduce significant risk to a company, particularly if they are not properly monitored and managed. In order to help mitigate these risks, companies can...
Where Applications Reside, Vulnerabilities Arise – Network Services
Firewalls are considered to be a blocking control on our networks, but inherently also exists to allow users access to functionality; functionality provided by applications. Applications unfortunately regularly contain vulnerabilities,...
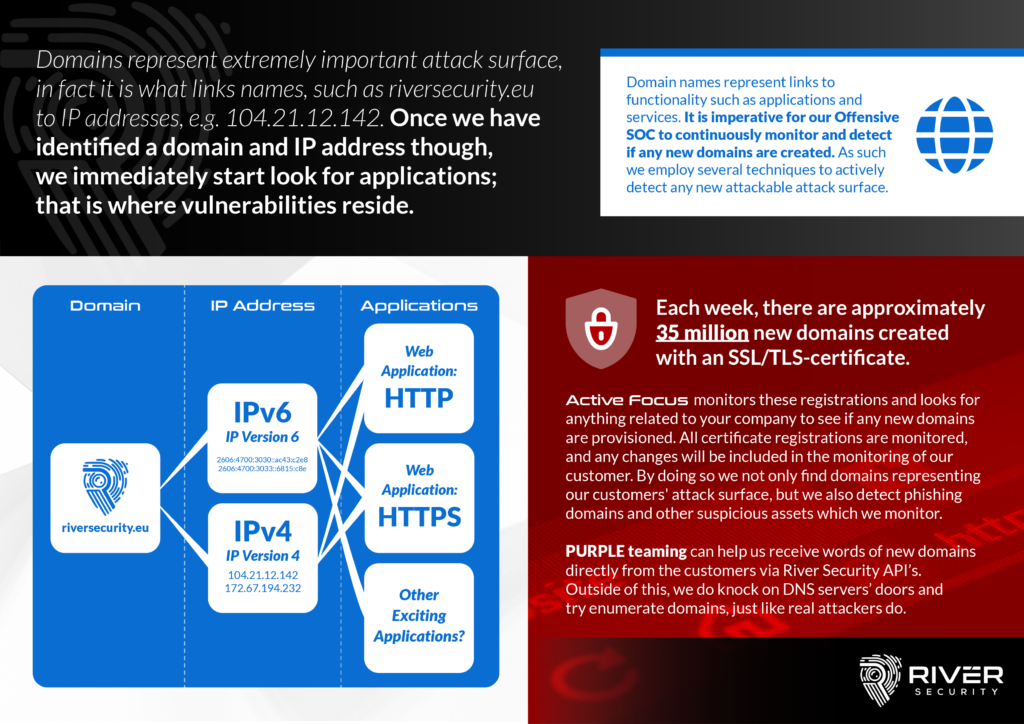
Why Do We Monitor for Domains? Finding Keys to the Kingdom!
Domains represent a crucial and vital part of the attack surface our organizations expose. A DNS ("Domain Name System") is a central part of every organization and can essentially be...
Users and Cyber Threat Intelligence
Cyber Criminals Can Do It, So Can We! Is there any new opportunities Cyber Threat Intelligence provide our Offensive Engineers? On a regular basis, organizations are compromised because of credentials...