Posts by
Chris Dale
Why We Monitor Technology
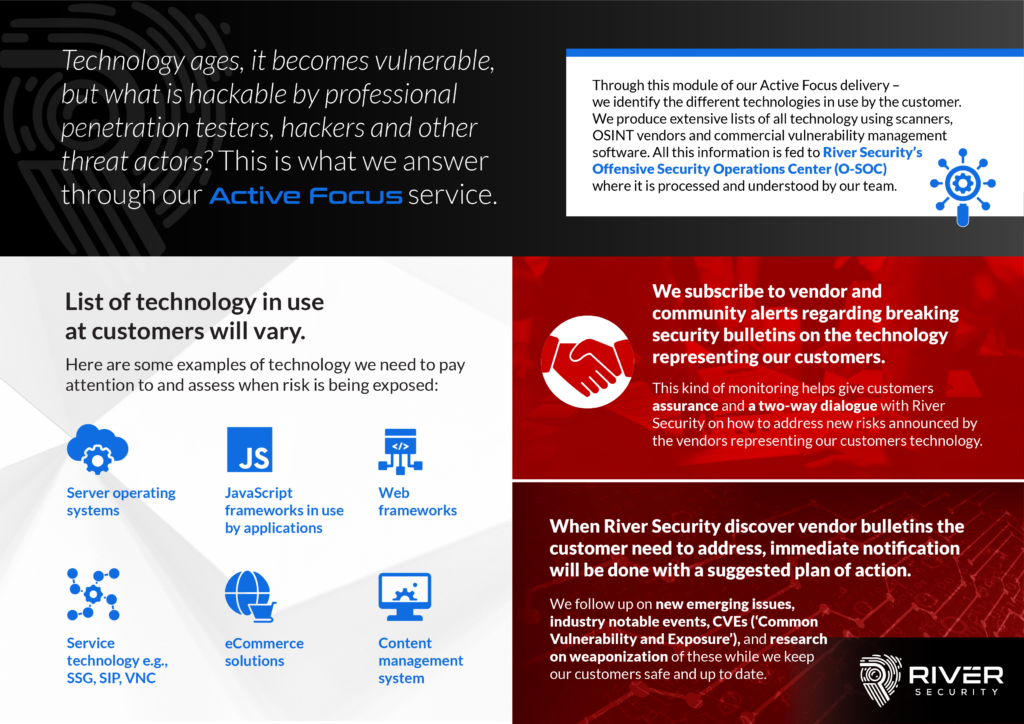
A key pillar in every organizationTECHNOLOGY Why and how do we monitor it? What kind of opportunities does it present our Offensive Security Operations Center? With aged technology comes vulnerabilities....
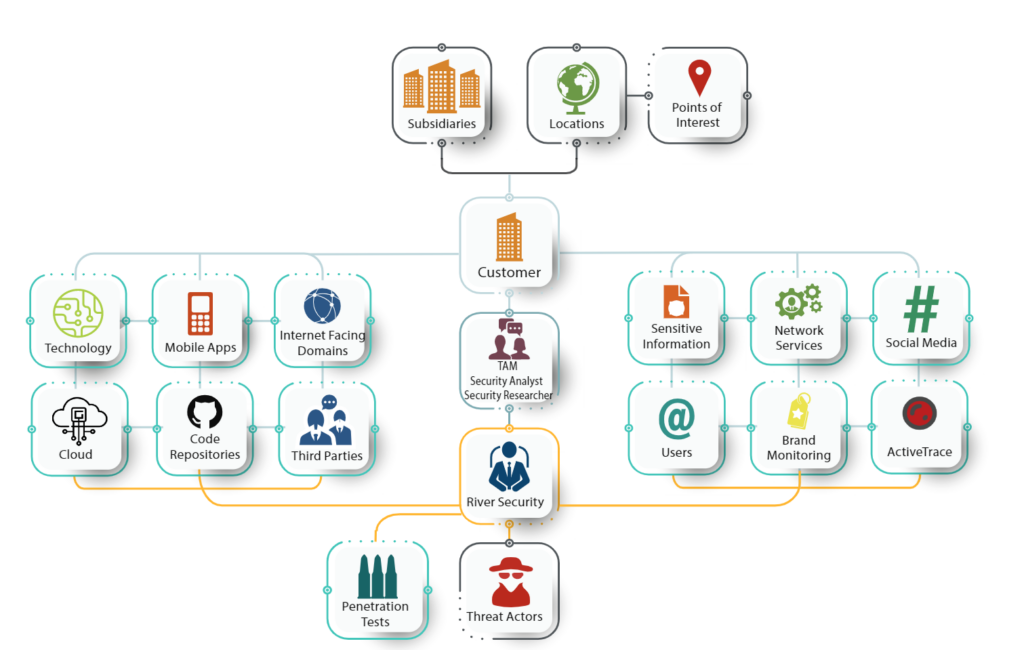
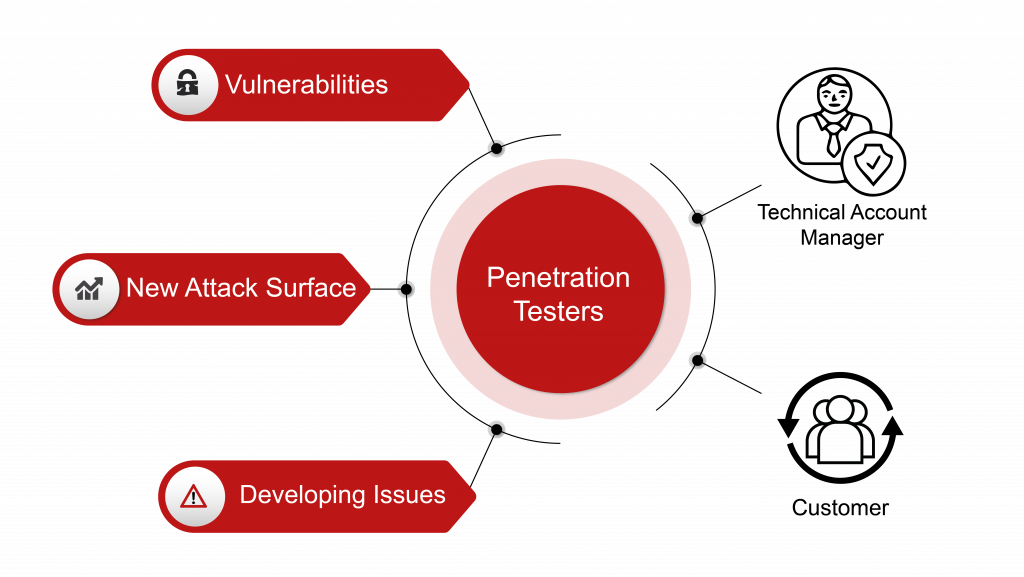
What is an Offensive Security Operations Center?
Penetration Testing exercises has for a long time has several flaws in its execution. For example: What is the scope of the penetration test? Who is best capable of setting...
❄River Security XMAS Advent Challenge ❄
The deadline, which was a short one, was set to the 27th of December, meaning only the most diligent and hard-working 🤶Santa’s little elves🎅 hackers would be able to participate...
Part 2 – Acquiring Talent in Information Security
This is a continuation of Part 1 - Acquiring Talent In Information Security. A Penetration Testing Wizard is assessing a new prospect Assessing New Prospects Being able to discern the...
Part 1 – Acquiring Talent In Information Security
Hiring Great Fantastic Penetration Testers What does it take to become a successful penetration tester? How do you identify, hire and stimulate your staff? Did you know, some of the...
Karina Årland – Account Executive – Welcome!
We are incredibly happy to announce our latest member to the team, Karina Årland, joining us from Beerenberg! We welcome her to the position as Account Executive. The continuous growth...
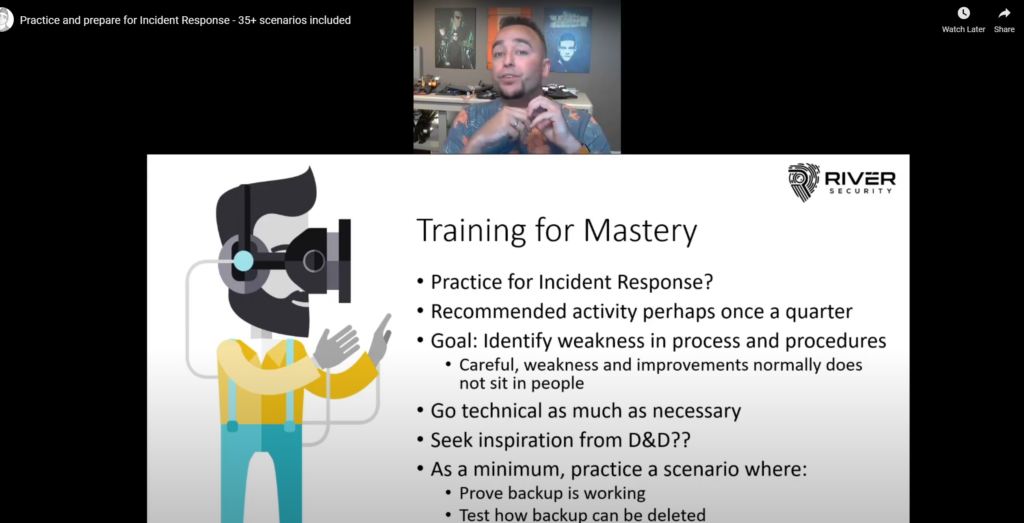
Incident Response – Practicing and Gamification
I recently published a video on YouTube on the aspect of practicing Incident Response scenarios, applying elements of gamification and planning out how we can plan to prepare against dealing...
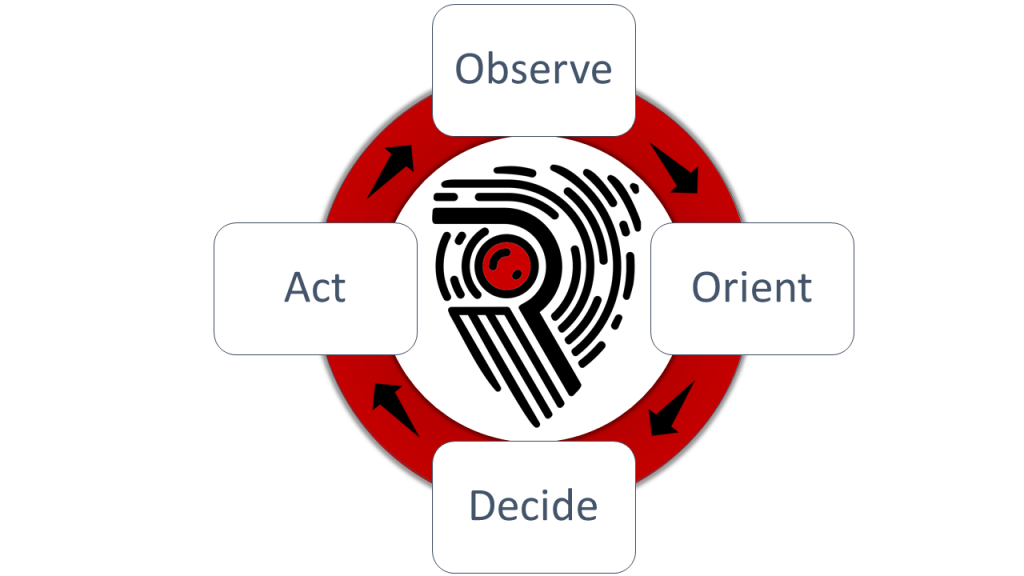
OODA Loops, Speed and Agility
To beat attackers at their own game, it is imperative River Security is able to more rapidly detect, uncover and find flaws in our customers environments than the threat actors....
Know Your Enemy
River Security follow closely the attackers' behaviors and attack techniques. In studying attackers Tactics, Techniques and Procedures (TTP's), our tools are sharpened and tailored to discover weaknesses in organizations defenses...
Cyber Warfare – The threat of the 0-day – Is there nothing we can do?
Introduction Breaking news within our Cyber Security domain has become almost an everyday business; Cyber-Warfare and crime has become an everyday threat against democratic values, privacy and the livelihood of...