What is an Offensive Security Operations Center?
Penetration Testing exercises has for a long time has several flaws in its execution. For example:
- What is the scope of the penetration test?
- Who is best capable of setting the scope?
Clients are often not the best to answer the question regarding what the scope is. If they were, we would not have the problem of Shadow IT and Dark Data. To combat this, we invented the Digital Footprint exercise, allowing companies to better grasp their data awry, systems unmaintained and other long-hanging fruits attackers can potentially abuse if they were to look.
Our Offensive Security Operations Center was designed to continuously, every day and hour, let our customers know which opportunities exists in attacking them, but with as close to zero to no false-positives. Always accurate alerts on where and what our customers should address concerning their own risk.
The Offensive Security Operations Center
Our team will dedicate efforts in demonstrating the effects of vulnerabilities so informed actions can be put in motion by our customers. The following graphic shows some of the areas of opportunities in which our team, from day-to-day business, assesses and builds automation, procedures and process on how to both discover assets and help uncover risks in them.
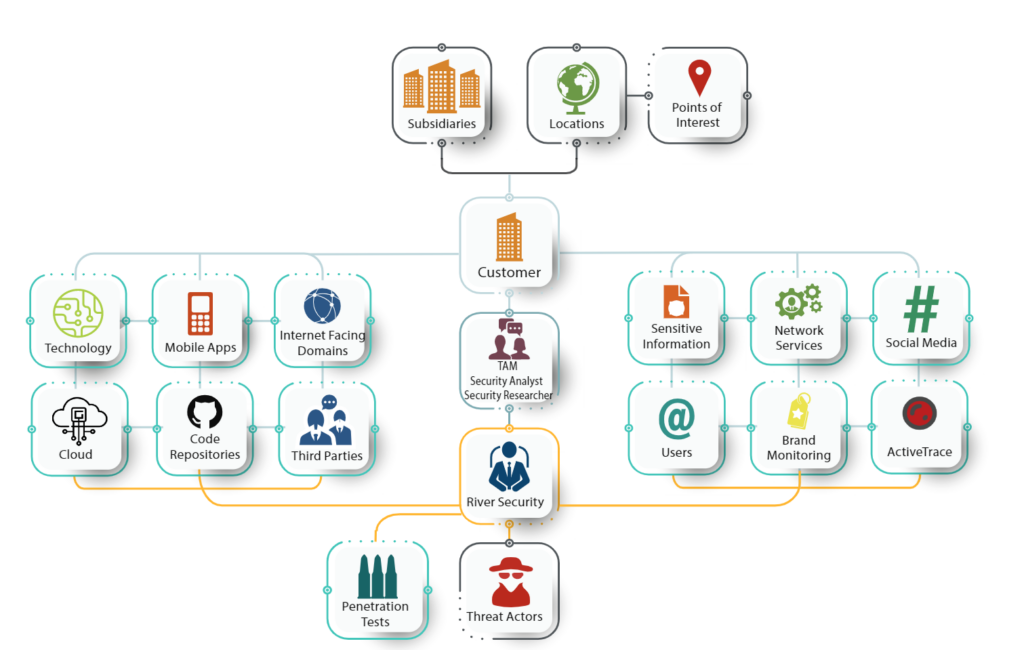
Each of these blocks contain automation and data-gatherers which helps the team focus, on a continuous basis, on the assets which change. Let us look into a few of them.
Technology
Assets come with a range of technology, i.e. software, installed on them, each which has security updates put forward by the developers on a consistent basis. Some of these security updates are highly critical and requires immediate attention, while others, in fact most of vulnerabilities, can safely be patched via the organizations defined patch management processes.
River Security’s team of offensive security personnel helps assess technology and vulnerabilities everyday, asking the question “can the customer suffer from this” many times a day. In fact, we employ licensed vulnerability scanners and parse the results, subscribe to the latest updates in the threat landscape (i.e. CVE, Common Vulnerabilities & Exposure) and we stay on top of the current Cyber Threat Intelligence when there are developing issues in the world.
Our bottom line, and so should yours, is asking ourselves the question: “Can we hack you?“. Rest assured, our team is trained and capable, every day watching over our customers, trying to hack them.
Other Modules and Data Points
We employ a lot of automation to collect data, using agents running off a multitude of different infrastructure to allow us unfederated collection and scanning. Many of our data points come from partnerships and paid sources of data, giving River Security as much data and opportunities to secure our customers against threat actors as possible.
Among the many things we check for, and for the sake of brevity in this post, we have listed a couple of highly important aspects of our service which we continuously monitor:
- New network services appearing within a customers attack surface, i.e. ports opening and closing.
- Domains registered which represents our customers brand, sometimes phishing domains set up to trick users and customers, but also systems provisioned by DevOps to be accessible by users. Each and every item thoroughly tested and vetted by River Security’s offensive personnel.
- Data Leaks, e.g. credentials, allowing attackers opportunities to log into services as otherwise benign users.
Because River Security works as a Red Team, an offensive unit trying to break in, but on a contract with customer, together with the Blue Team, the defending party, great synergies happen. Customers in many cases allow us to enumerate, e.g. the cloud, from the inside, providing us with a highly accurate asset inventory which we will target, scan and attack from the outside, preventing mistakes and vulnerabilities to surface on the Internet.
The Team and Reporting
We do not necessarily believe in “yet another dashboard” for customers to log into to receive or understand their current threat landscape. Instead, our team works in our customers preferred way of receiving alerts, all of which are custom written by our specialists to ensure our customer fully understands the ramifications. Furthermore, manual reporting helps guarantee our customers always receive actionable reports and knowledge transfer which helps the longevity of our customers security operation.
This kind of reporting, thinking and working allows the previous traditional and slow penetration test exercise to take a new form, inspired by agility and continuous changes, not snapshots and limited scopes of work.
Contact us today and see for yourself. A 30 minute meeting with us will help you see and understand your own digital footprint and help you in gaining an understanding and resolve of what to do next. Where should your IT Security maturity take you next? Attack Surface Management and Always-On penetration testing is the answer for most businesses which seek to prosper and grow their online digital presence.
