Users and Cyber Threat Intelligence
Cyber Criminals Can Do It, So Can We! Is there any new opportunities Cyber Threat Intelligence provide our Offensive Engineers? On a regular basis, organizations are compromised because of credentials...
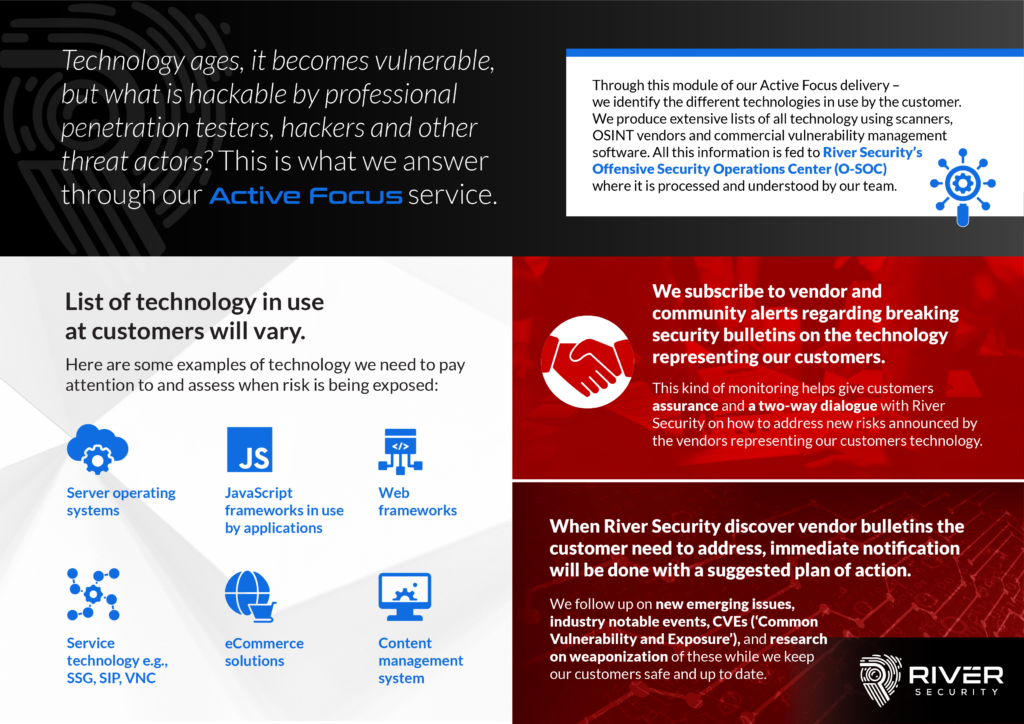
Why We Monitor Technology
A key pillar in every organizationTECHNOLOGY Why and how do we monitor it? What kind of opportunities does it present our Offensive Security Operations Center? With aged technology comes vulnerabilities....
The Infosec & OSINT Show – Breaking up the recon and pentest produces better results
Today the podcast Infosec & OSINT show was released, and our Founder and Principal Consultant Chris Dale participated on the show. He explains why breaking up recon and pentest produces...
How to engage a company in Offensive Services
This post will assist you in how to best start engaging a company in offensive services, because you want to understand the running risks of your company. It highlights how...
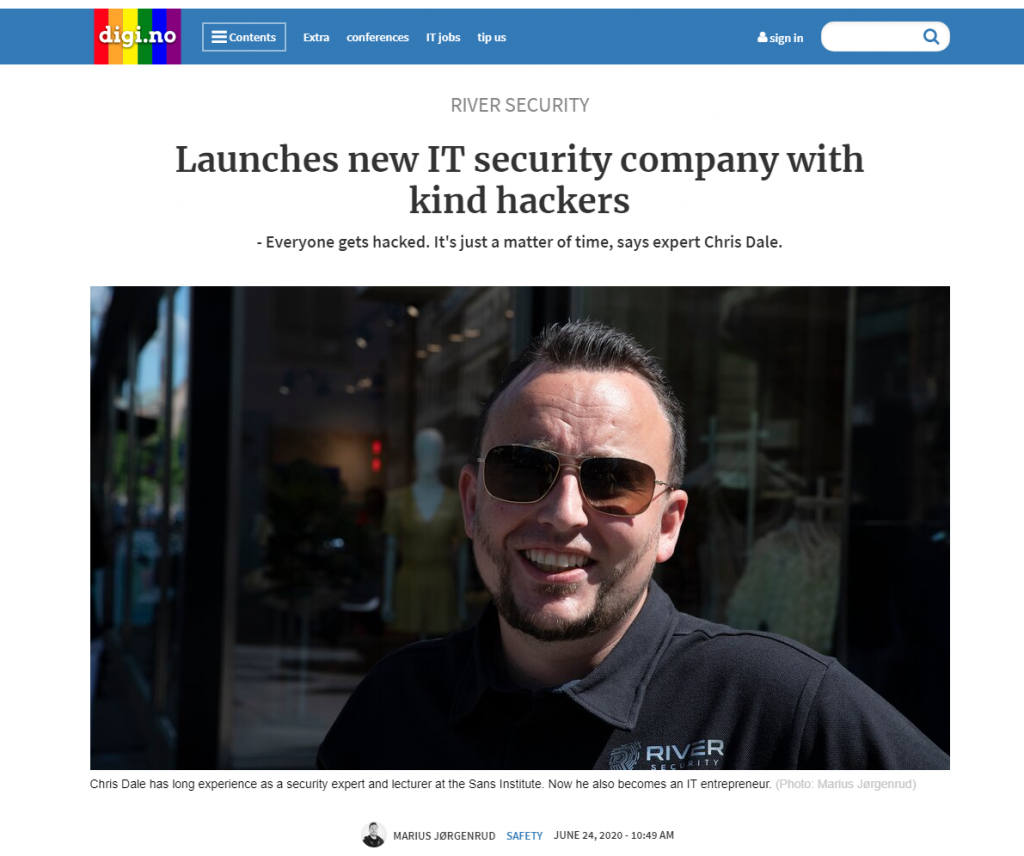
“Everybody will be hacked, it’s just a matter of when, not if” – Interview Digi.no
Today we were featured in an article on a Norwegian online magazine called Digi.no. The article discusses our company launch and some important distinctions that makes us different from many...
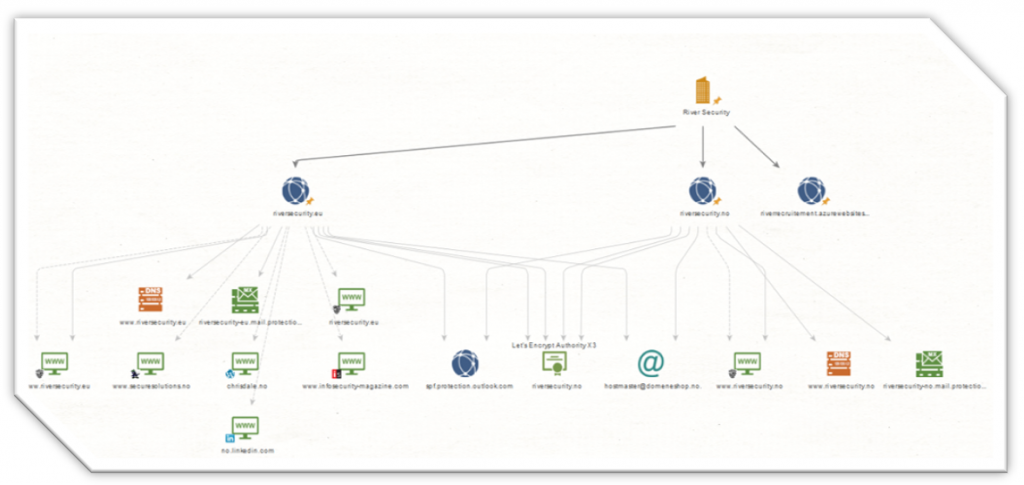
Digital Footprint – The first step in most offensive services – Guest Blog Post
We've contributed with a blog post at www.sans.org to shed light on smarter, more efficient and convenient ways of providing offensive services. We discuss the mutual benefits of mapping the...