River Security
Where Applications Reside, Vulnerabilities Arise – Network Services
Firewalls are considered to be a blocking control on our networks, but inherently also exists to allow users access to functionality; functionality provided by applications. Applications unfortunately regularly contain vulnerabilities,...
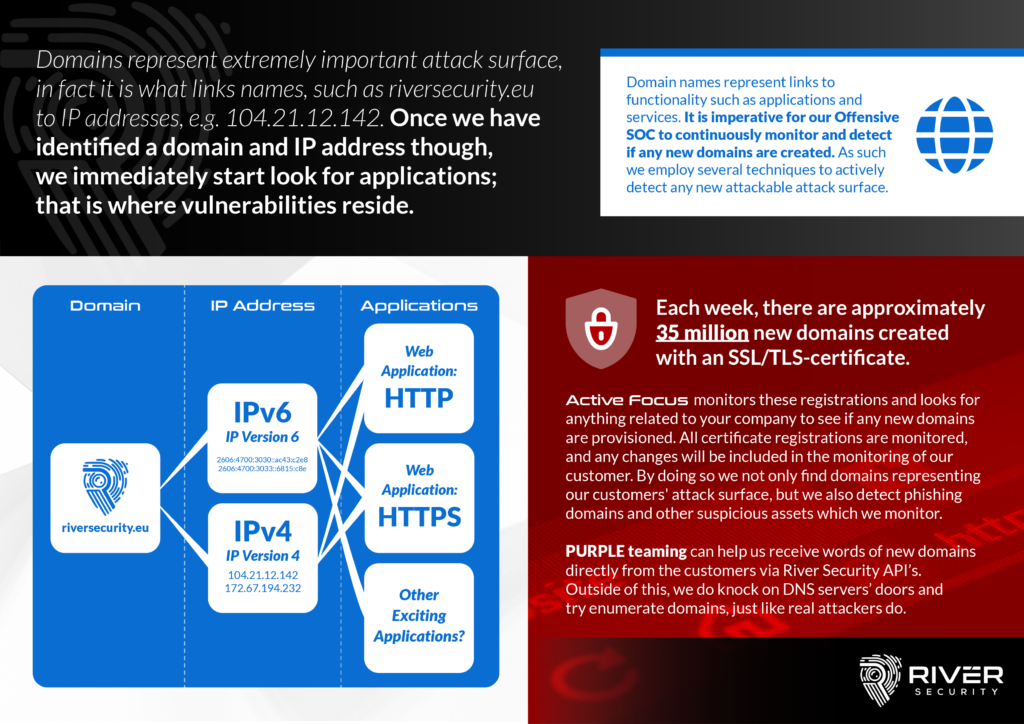
Why Do We Monitor for Domains? Finding Keys to the Kingdom!
Domains represent a crucial and vital part of the attack surface our organizations expose. A DNS ("Domain Name System") is a central part of every organization and can essentially be...
Users and Cyber Threat Intelligence
Cyber Criminals Can Do It, So Can We! Is there any new opportunities Cyber Threat Intelligence provide our Offensive Engineers? On a regular basis, organizations are compromised because of credentials...
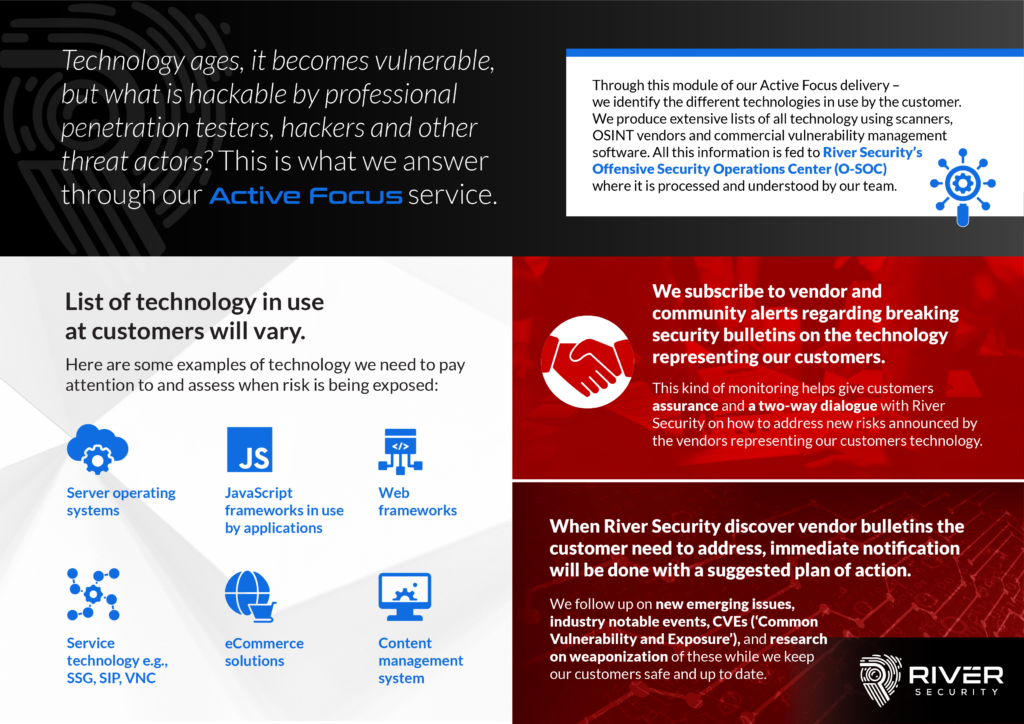
Why We Monitor Technology
A key pillar in every organizationTECHNOLOGY Why and how do we monitor it? What kind of opportunities does it present our Offensive Security Operations Center? With aged technology comes vulnerabilities....
We are looking for Senior Developers!
Are you passionate and experienced in development and architecture? Perhaps have a special thing for Cyber Security too? You might be the person we are looking for! To support our...
Meet our Head of International Sales, Vegard Reiersen!
River Security has experienced substantial growth over the past two years. Our services are gaining increasing international attention and demand, and we are super happy to finally announce Vegard as...
Two years in business
River Security is all about upstream thinking, thinking ahead of the symptoms and fixing problems at their core. Combating Adversaries, The Way We Know Best “I do not believe in...
Efficiently Weaponizing Vulnerabilities and Automating Vulnerability Hunting
We want to congratulate our colleague, Simen Bai, who together with Ruben Christoffer Hegland-Antonsen and Even Bøe completed their Bachelor of Engineering in Computer Science at NTNU! The bachelor thesis...
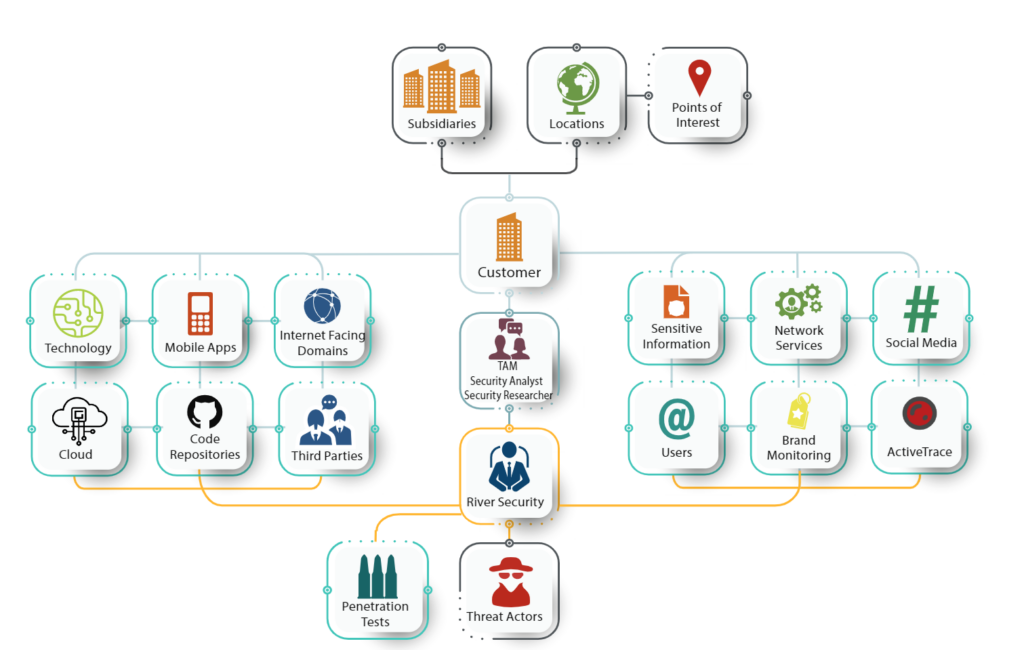
What is an Offensive Security Operations Center?
Penetration Testing exercises has for a long time has several flaws in its execution. For example: What is the scope of the penetration test? Who is best capable of setting...
A warm welcome to Robert!
We are happy to announce yet an expansion of the team! It is no secret that there is a global shortage in Cyber Security competence. It has been predicted that...