The challenge
A Timeless Methodology
Many methodologies have attempted to be a one-stop shop to test for all the possible ailments, often checklist driven and relying on having to know all the possible vulnerabilities in advance. What was researched and built through these methodologies today is likely outdated tomorrow.
Our methodology aims to put the penetration tester in the research driving set, enabling them to focus and prioritize their efforts through a range of more abstract steps, rather than individual checklists of findings and out-dated steps.
Checklists can be useful helpers and guides, but not the sole solution, but as part of a more abstract methodology.

The solution
A Research Centric Timeless Methodology
How do you build fantastic penetration testers? By teaching them everything you know? Or by teaching them how to learn everything you know? Naturally, we gravitate to the latter. Building a robust methodology to enable penetration testers to explore, discover and do what true hacking should be all about it essential.
The methodology River Security has developed represents an upside down pyramid. Each step of the pyramid indicates in a general sense how much time and efforts are being put into it. As an example, content discovery implies reconaissance, scanning, and discovery of assets, this is the most time consuming phase. Conveniently, this is also the phase customers can help the most on, enabling purple teams and more efficient penetration testing.
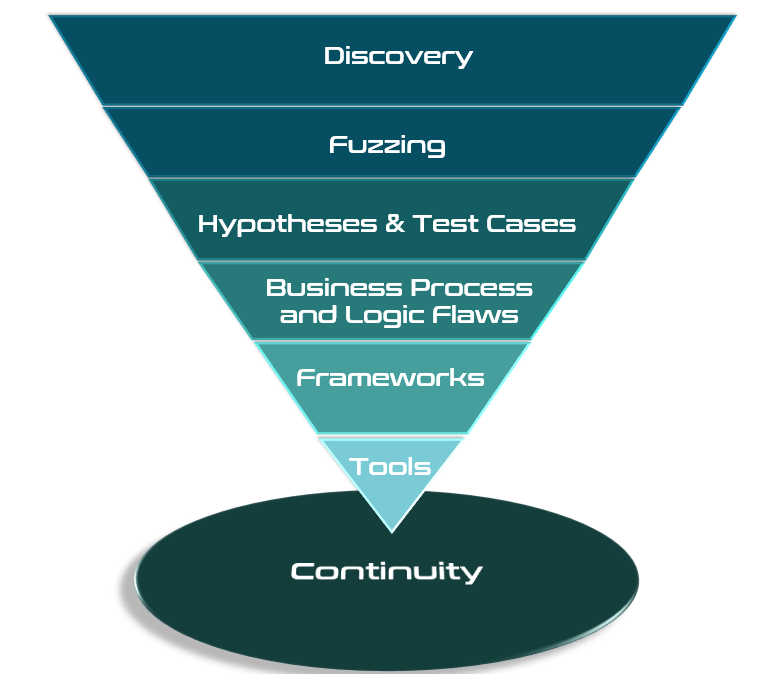
More Than Just Checklists and Tools!
Penetration testing goes beyond simply ticking boxes on a checklist or running automated tools. It’s about stepping into the mindset of a malicious actor and understanding the unique context of each application. While tools help automate repetitive tasks and checklists promote thoroughness, the real value lies in the tester’s creativity, intuition, and problem-solving skills.
This human-driven approach uncovers complex and hidden vulnerabilities that automated tools often overlook. Effective penetration testing demands a deep understanding of systems, adaptability to evolving threats, and a relentless curiosity to find the unexpected.

The results
Creating Rock Star Testers and High Quality Results
Parts of this methodology is to ensure that no penetration test relies on a single individual to complete; it has to a be a team effort. Utilzing the team helps ensure competency is activated where it should be, and allows members to escalate interesting artifacts and possible vulnerabilities to other team members.
Our customers rely on receiving high quality results as it is unacceptable for us to no provide value equal to the work we provide. At River Security we are known for being frank, honest and up front with the problems we discover, ensuring knowledge transfer and understanding during and after our engagements.
Success Stories
Customer Cases

Take the next step with your business today with Active Focus
Having a team of ethical hackers poke and probe at your brand, your organizations, and your assets is typically an invaluable experience. Let us find the weaknesses before the real attackers do; contact us today!
