River Security
Say hi to Martin
We are happy to announce that Martin Andreassen has joined River Security as a Business Developer. Martin is an INSEAD MBA with significant international exposure, having lived and worked in...
Ethical Considerations in Incident Response
Ethical considerations in incident response, especially when dealing with sensitive data and disclosing information about security breaches, are paramount. These situations require a careful balance between transparency, confidentiality, legal obligations,...
Welcome William
We are delighted to introduce William Kristoffersen as our latest team member, stepping into the role of Senior Penetration Tester! Through thorough interview rounds and his active participation in our...
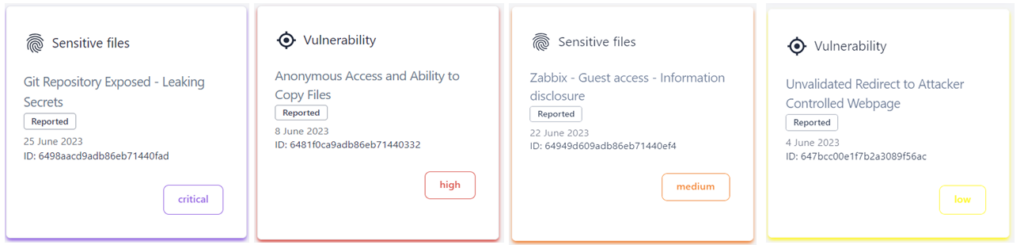
Navigating the Currents of Cybersecurity: River Security’s Approach to Distinguishing Vulnerabilities, Security Hygiene, and Exploitable Issues
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats requires a keen understanding of the nuanced differences between vulnerabilities, security hygiene, and issues with demonstrable impacts on confidentiality,...
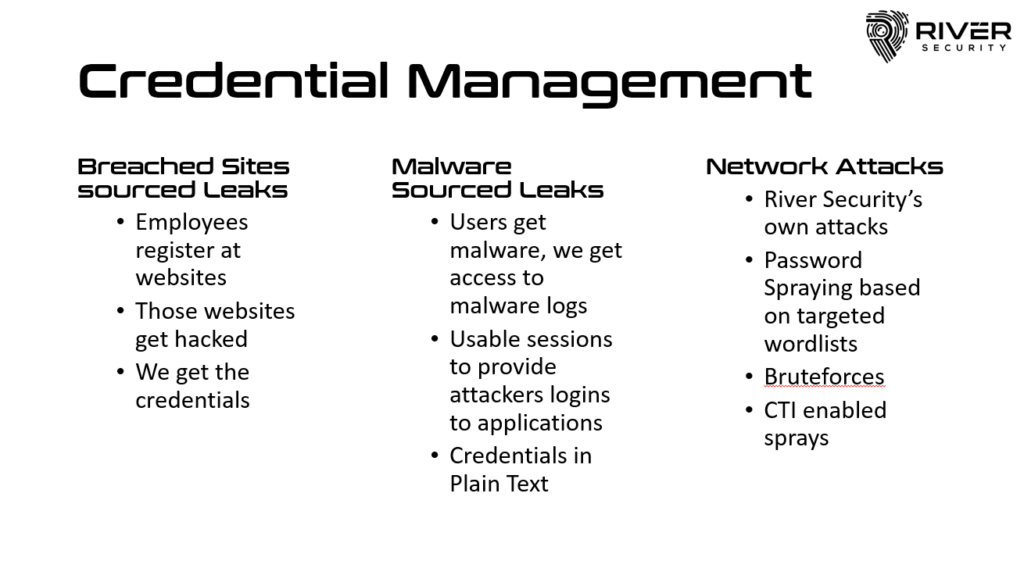
Strengthening the Fort: How Attack Surface Management Empowers Companies in Web Security, Mail Security, Credential Management, and Authentication
There are many "vulnerabilities" that don't need immediate fixing; best practices, security hygiene and many other priorities risk taking priority over other more important security factors. At River Security, we...
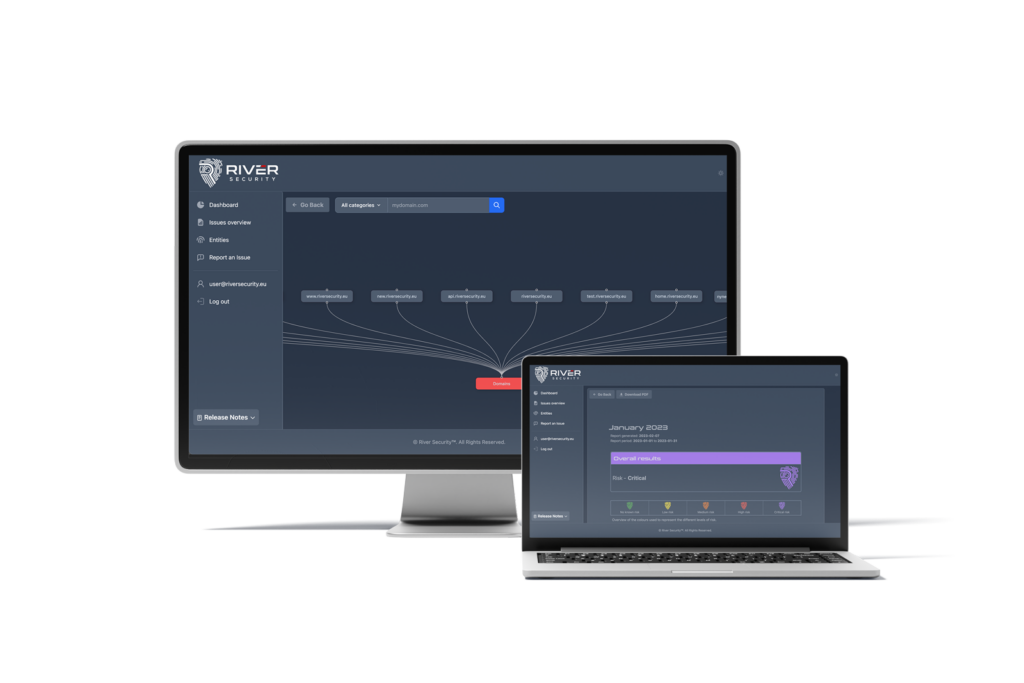
Beyond Bug Bounty – Elevating Security with Attack Surface Management
In an era where cybersecurity threats constantly evolve, organizations must stay ahead of malicious actors to safeguard their digital assets. Bug bounty programs have surged in popularity recently as a...
River Security Joins the Norwegian Cybersecurity Cluster
In today's interconnected digital landscape, the importance of robust cybersecurity measures cannot be overstated. With the ever-evolving threat landscape, collaborative efforts and shared expertise are essential to ensure the safety...
Changes to the Board of Directors
Change is a constant factor within any active organization, and at River Security, we're glad to share a shift in our board that pushes us toward a future filled with...
The Illusion of Security
Why SOC Can Give False Confidence Compared to Proactive Offensive Services In the rapidly evolving landscape of cyber security, businesses face an ever-increasing number of threats that can compromise their...
Introducing Cato Stensland – A Security Maverick with a Vision
We are thrilled to announce our newest addition to the team, Cato Stensland, who is joining us as a Threat Intelligence Manager. With a remarkable background in the Intelligence Service...