Strengthening the Fort: How Attack Surface Management Empowers Companies in Web Security, Mail Security, Credential Management, and Authentication
There are many “vulnerabilities” that don’t need immediate fixing; best practices, security hygiene and many other priorities risk taking priority over other more important security factors. At River Security, we differenciate between actual issues which require prioritization, and other items, often security hygiene issues which are useful to know about, but doesn’t require anyone yelling at you to prioritize fixing of.
Attack surface management (ASM) is as a powerful ally, especially when used as fuel to penetration testing teams with continious streams of information to enable them to penetration test. This information can be extremely useful, not only to penetration testers, but for daily operations and life-cycle management of our entities.
Web Security and Best Practices
Web security is the cornerstone of most applications today; it has quickly become ubiquitous. During our assessments, leveraging automation and scanning, we also naturally find information on wether or not web security best-practices are implemtend or if they are neglected. As we scan and discover systems, web applications are scrutinized by the automated tools penetration testers utilize to help prove risks to our clients; this data is forwarded into the Attack Surface Management tool, allowing us to report on the current security-state of the web applications best practices.
These best practices are plentiful, and some examples are highlighted below:
- Does the website limit and control which JavaScript is allowed to run via Content Security Policies?
- Is there any HTTP Strict Transport Security enabled?
- What about server and header information revealing the details about the technology running on the system?
- Is there a permanent redirect to HTTPS?
Providing visibility and helping customers understand and manage these risks is useful to create resilient and “water tight” attack surfaces. We not only poinpoint potential weaknesses, but assit the organization in implementing these best practices.
Mail Security
Email remains a primary vector for cyber attacks, making mail security a critical concern for organizations. Our Attack Surface Management technology plays a pivotal role in helping companies manage and organize their email security defenses. By mapping out the attack surface related to email systems, organizations can identify potential entry points for malicious actors and implement robust controls to mitigate risks.
River Secruity facilitates the monitoring of email security protocols, enabling companies to enforce strong encryption, implement anti-phishing measures, and detect anomalous activities. Through continuous scanning and assessment, River Security provides the opportunity for security and optimization; empowering organizations to organize and fortify their mail security, reducing the risk of data breaches and unauthorized access.
We help customers understand vital information surrounding their domains email security policies, such as:
- Domains should have a NoMX record if they are not sending emails
- DMARC, DKIM and SPF should have proper configurations
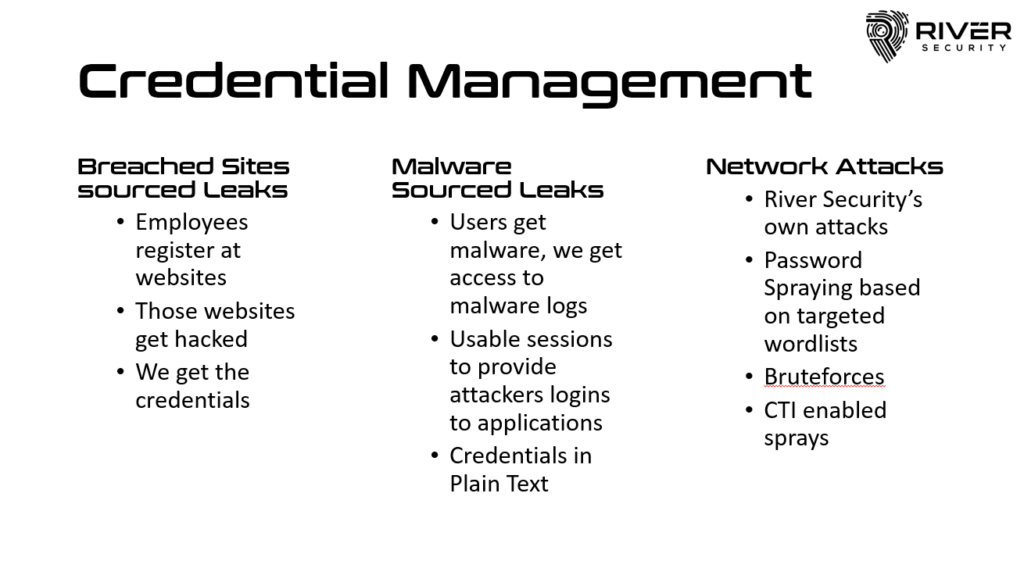
Credential Management
Effective credential management is essential for safeguarding sensitive information and preventing unauthorized access. River Security receives and tests large lists of credentials on behalf of our users and their applications all the time. Such accounts we help can be protected behind Multi Factor Authentication and Password Resets.
Using our Active Focus service provides a comprehensive view of an organization’s attack surface, helping companies identify weak credentials that work across the attack surface. By organizing breach and credential data, testing them and providing our customers with actionable evidence, we take away valuable and important key tactics, techniques and procedures from the threat actors.
River Security’s role in credential management extends beyond identification to proactive defense. It enables organizations to organize and implement strategies for password rotation once breach is a fact, and employee training on secure authentication practices. For several of our customers, it even enables them to proactively help their customers secure their credentials, as such data is also presented by River.
Authentication
River Security empowers companies to manage and organize authentication processes by providing insights into potential vulnerabilities and weaknesses in their systems, for example what authentication is supported over FTP, SSH and other protocols. Organizations can leverage our platform to conduct risk assessments and implement controls that strengthen the authentication process. This includes organizing assets so that necessary strategies for implementing proper defensive measures can be implemented.
Security Hygiene
At River Security we differentiate between vulnerabilities, actual impact to the target, and hygienic issues. It is important to not over report on vulnerabilities, crying “wolf, wolf” for everything, because it tends to leave our security teams incapable of prioritizing correctly. Ideally we would like to patch and keep everything in order, as long as we would just know what to fix, but realitiy is that we don’t have time and capabilities to keep everything updated. Instead, we differentiate between the vulnerabilities, security hygiene and things we would like to fix, with actual vulnerabilities with a demonstratable effect against confidentiality, integrity or availability.
