Why Cyber Due Diligence is Critical for M&A Success
[Editor's Note: Even Andreassen is one of our talented business developers. He is also an assistant professor at a Norwegian university. In this excellent blog post he has given us...
Finding Attack Surface and Other Interesting Domains via Certificate Transparency Logs
Certificate Transparency (CT) logs are like public records for internet security. When a new TLS certificate is issued, it gets logged in these CT logs. This makes it easier for...
Protecting Your Data: Techniques for Securing Sensitive Information Online
Data has become the currency of our time and as such, it is crucial to ensure its security. Hackers can easily gain access to highly sensitive data through simple Google...
Don’t Overlook Social Media Security: Protecting Your Brand
Social media has emerged as a significant yet often overlooked part of the attack surface for many businesses. Understanding where your brand is exposed online is crucial to safeguarding these...
Code Repositories: A Wealth of Information and Potential Threats. How River Security Protects Your Assets
At River Security, one of our key priorities is helping our customers protect their assets and data from potential threats. One way we do this is by identifying customer-owned code...
Mobile Apps Can Reveal Valuable Information for Attackers
Mobile applications have become a crucial part of modern business operations, with many companies relying on them to connect with customers, manage internal processes, and handle sensitive information. However, the...
Combating Digital Threats with Active Focus – Your Brand
Active Focus is designed to constantly monitor the digital attack surface of a business or organization, looking for signs of malicious activity or attempts to fraudulently use the company's brand....
5 reasons why you should explore Attack Surface Management
Co-writer: Vegard Reiersen The world is more digitally connected than ever before. Criminals take advantage of this online transformation to target the ever-changing digital attack surface and weaknesses in online...
Where Applications Reside, Vulnerabilities Arise – Network Services
Firewalls are considered to be a blocking control on our networks, but inherently also exists to allow users access to functionality; functionality provided by applications. Applications unfortunately regularly contain vulnerabilities,...
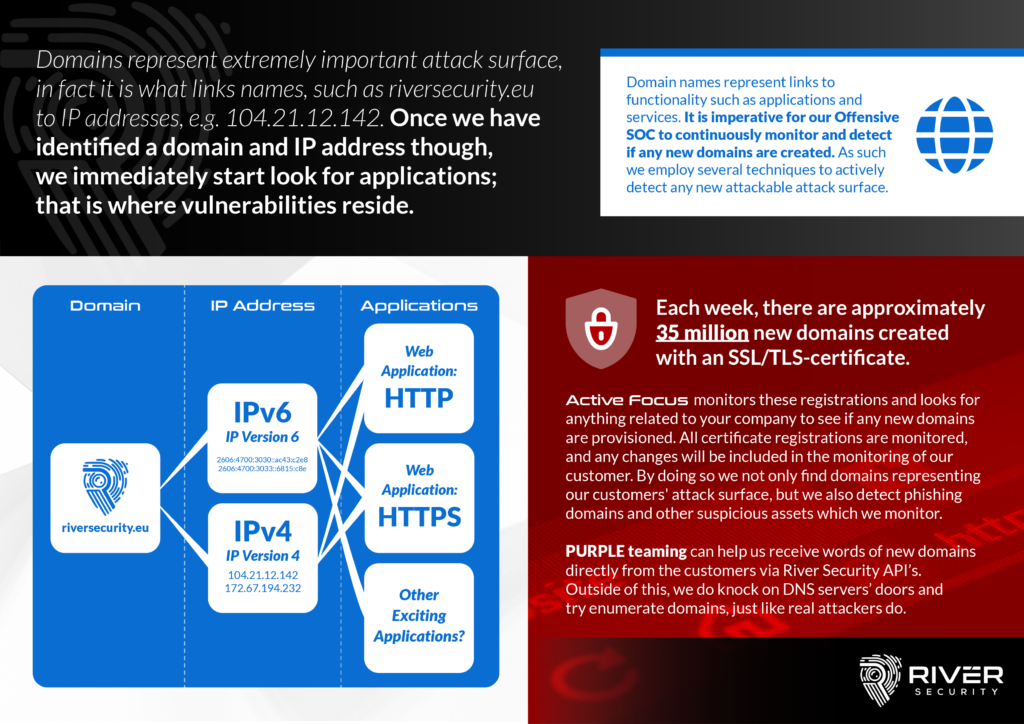
Why Do We Monitor for Domains? Finding Keys to the Kingdom!
Domains represent a crucial and vital part of the attack surface our organizations expose. A DNS ("Domain Name System") is a central part of every organization and can essentially be...