Penetration Testing
5 reasons why you should explore Attack Surface Management
Co-writer: Vegard Reiersen The world is more digitally connected than ever before. Criminals take advantage of this online transformation to target the ever-changing digital attack surface and weaknesses in online...
Where Applications Reside, Vulnerabilities Arise – Network Services
Firewalls are considered to be a blocking control on our networks, but inherently also exists to allow users access to functionality; functionality provided by applications. Applications unfortunately regularly contain vulnerabilities,...
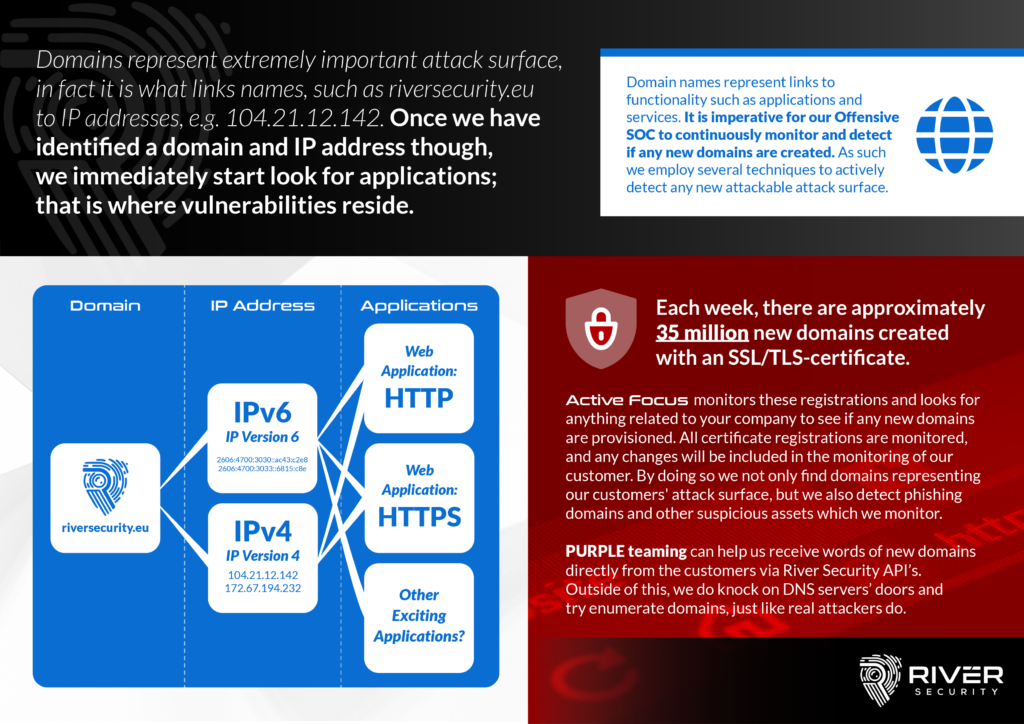
Why Do We Monitor for Domains? Finding Keys to the Kingdom!
Domains represent a crucial and vital part of the attack surface our organizations expose. A DNS ("Domain Name System") is a central part of every organization and can essentially be...
Users and Cyber Threat Intelligence
Cyber Criminals Can Do It, So Can We! Is there any new opportunities Cyber Threat Intelligence provide our Offensive Engineers? On a regular basis, organizations are compromised because of credentials...
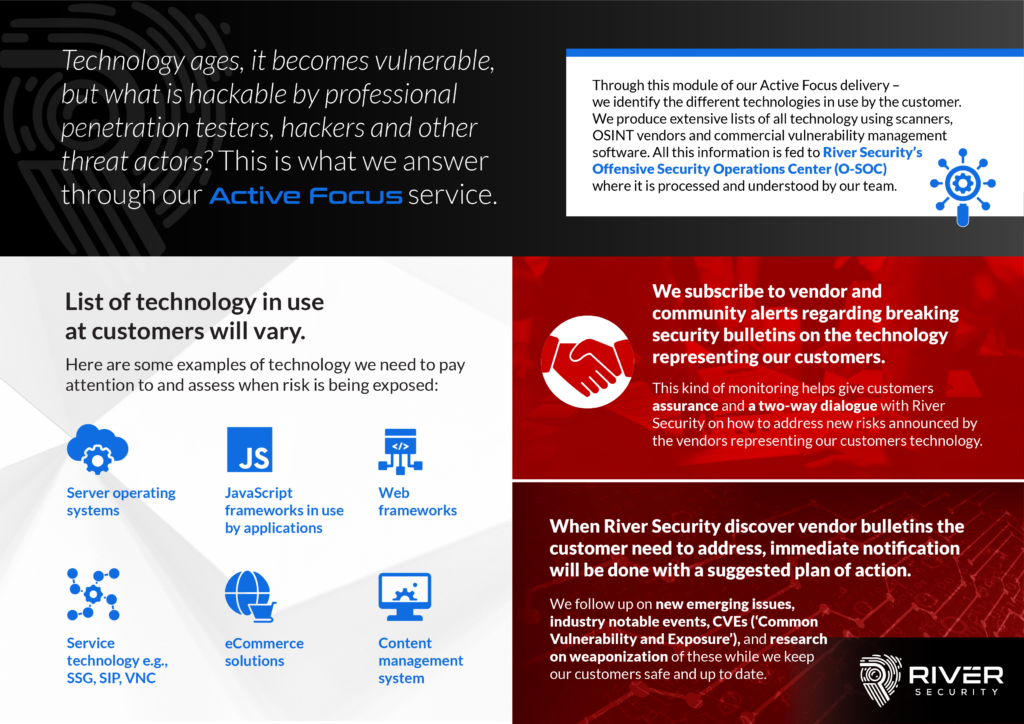
Why We Monitor Technology
A key pillar in every organizationTECHNOLOGY Why and how do we monitor it? What kind of opportunities does it present our Offensive Security Operations Center? With aged technology comes vulnerabilities....
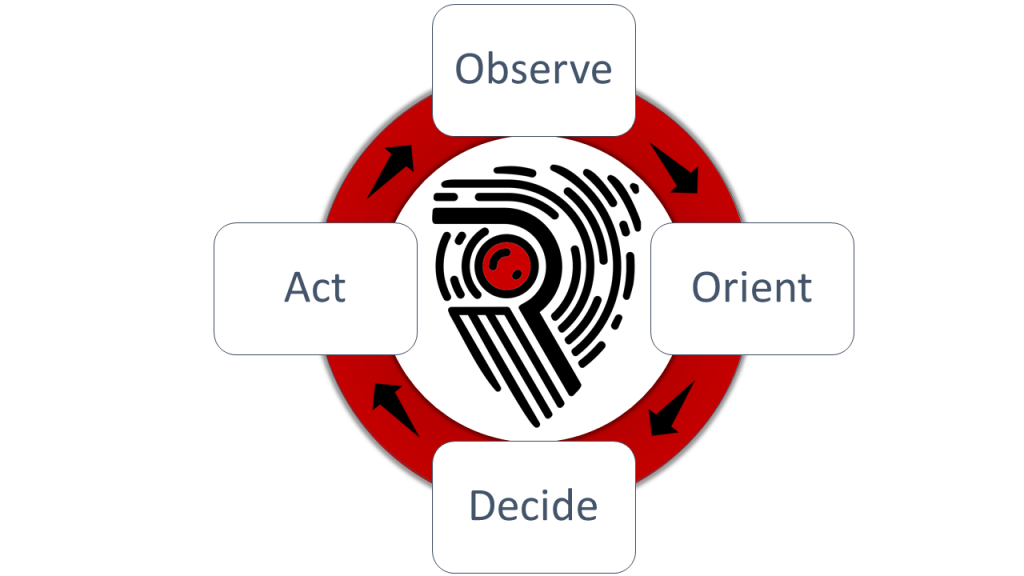
OODA Loops, Speed and Agility
To beat attackers at their own game, it is imperative River Security is able to more rapidly detect, uncover and find flaws in our customers environments than the threat actors....
Know Your Enemy
River Security follow closely the attackers' behaviors and attack techniques. In studying attackers Tactics, Techniques and Procedures (TTP's), our tools are sharpened and tailored to discover weaknesses in organizations defenses...
Ransomware Roulette – Level up or pay up
As we all know, at least to some extent, cryptocurrency solved the main problem (if we ask threat actors, that is) in ransomware and extortion attacks – getting away with...