SSL/TLS Management: Reducing Risks and Gaining Visibility
Transport Layer Security (TLS) and its predecessor SSL remain cornerstones of modern internet security. They protect confidentiality, integrity, and authentication for data in transit. But while TLS is everywhere, managing...
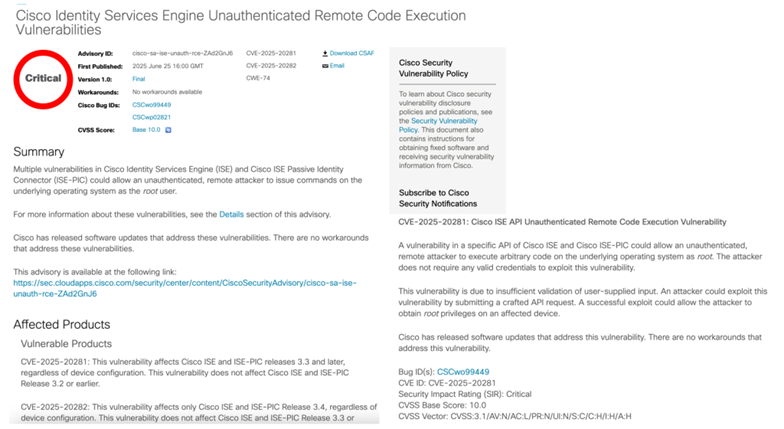
Like stealing (Cisco) ISE-cream from a kid – Weaponizing a CVE
[Editors Note: Raymond Strandheim is a principal pentester, and I asked him to share with us how he managed to weaponize a new vulnerability from Cisco into a working exploit...
Why Cyber Due Diligence is Critical for M&A Success
[Editor's Note: Even Andreassen is one of our talented business developers. He is also an assistant professor at a Norwegian university. In this excellent blog post he has given us...
Pentesting is Transforming: 8 Steps to a Successful Pentest Operation in 2025!
Pentesting isn’t what it used to be, folks. Gone are the days of single checklist exercises and surface-level scans. In 2025, we’re transforming the way we think about pentesting—making it...
The Art of Discovery: A Penetration Tester’s Journey Through a Django Misconfiguration
[Editors Note: Eirik Valle Kjellby is an amazing gentleman and the latest, as of October 2024, addition to the ever growing penetration testing team at River Security. He continues to...
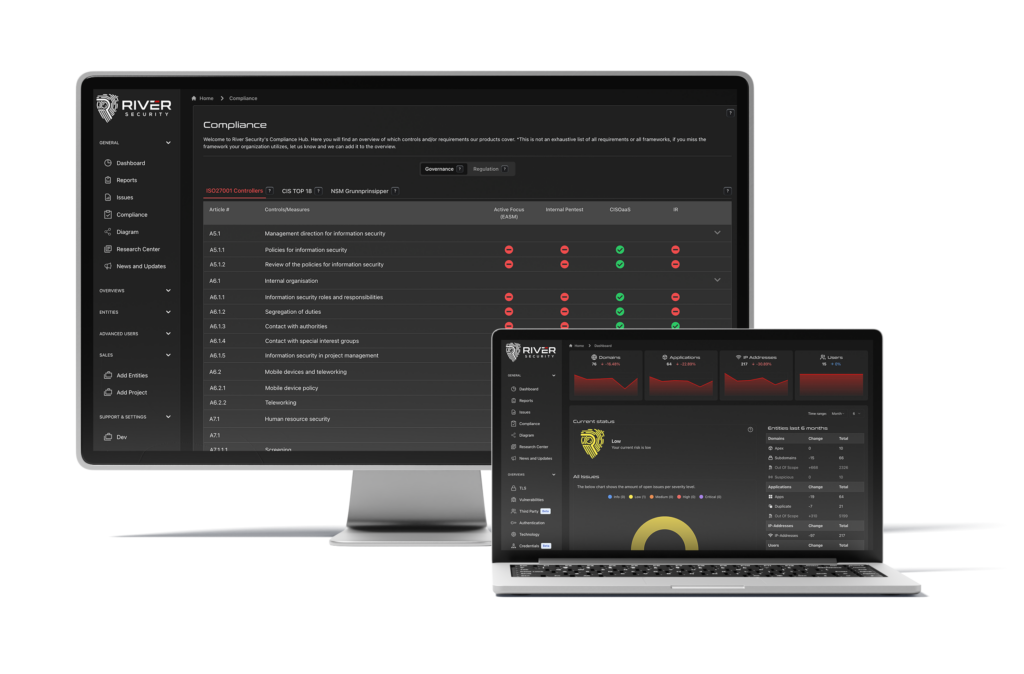
Guide to Navigate the Most Common Frameworks and Regulations for Cyber Security
In this comprehensive guide I will go through the most common frameworks and regulations for Cyber Security, as there might be some confusion in how to apply them to the...
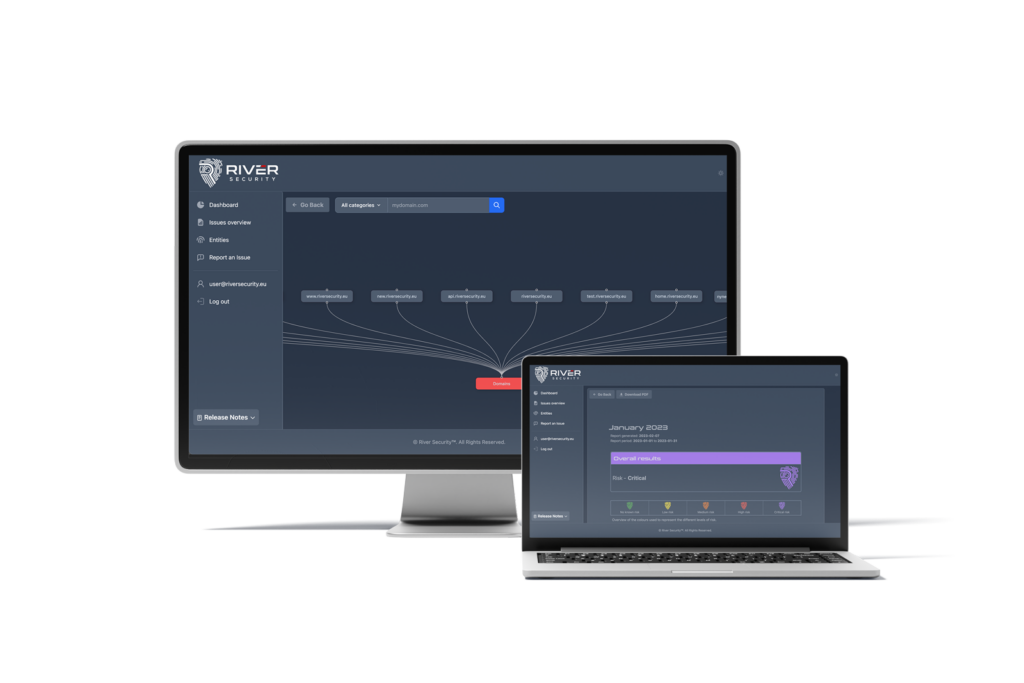
Finding Attack Surface and Other Interesting Domains via Certificate Transparency Logs
Certificate Transparency (CT) logs are like public records for internet security. When a new TLS certificate is issued, it gets logged in these CT logs. This makes it easier for...
Beyond Bug Bounty – Elevating Security with Attack Surface Management
In an era where cybersecurity threats constantly evolve, organizations must stay ahead of malicious actors to safeguard their digital assets. Bug bounty programs have surged in popularity recently as a...
Protecting Your Data: Techniques for Securing Sensitive Information Online
Data has become the currency of our time and as such, it is crucial to ensure its security. Hackers can easily gain access to highly sensitive data through simple Google...
Don’t Overlook Social Media Security: Protecting Your Brand
Social media has emerged as a significant yet often overlooked part of the attack surface for many businesses. Understanding where your brand is exposed online is crucial to safeguarding these...