SSL/TLS Management: Reducing Risks and Gaining Visibility
Transport Layer Security (TLS) and its predecessor SSL remain cornerstones of modern internet security. They protect confidentiality, integrity, and authentication for data in transit. But while TLS is everywhere, managing...
Pentesting is Transforming: 8 Steps to a Successful Pentest Operation in 2025!
Pentesting isn’t what it used to be, folks. Gone are the days of single checklist exercises and surface-level scans. In 2025, we’re transforming the way we think about pentesting—making it...
The Art of Discovery: A Penetration Tester’s Journey Through a Django Misconfiguration
[Editors Note: Eirik Valle Kjellby is an amazing gentleman and the latest, as of October 2024, addition to the ever growing penetration testing team at River Security. He continues to...
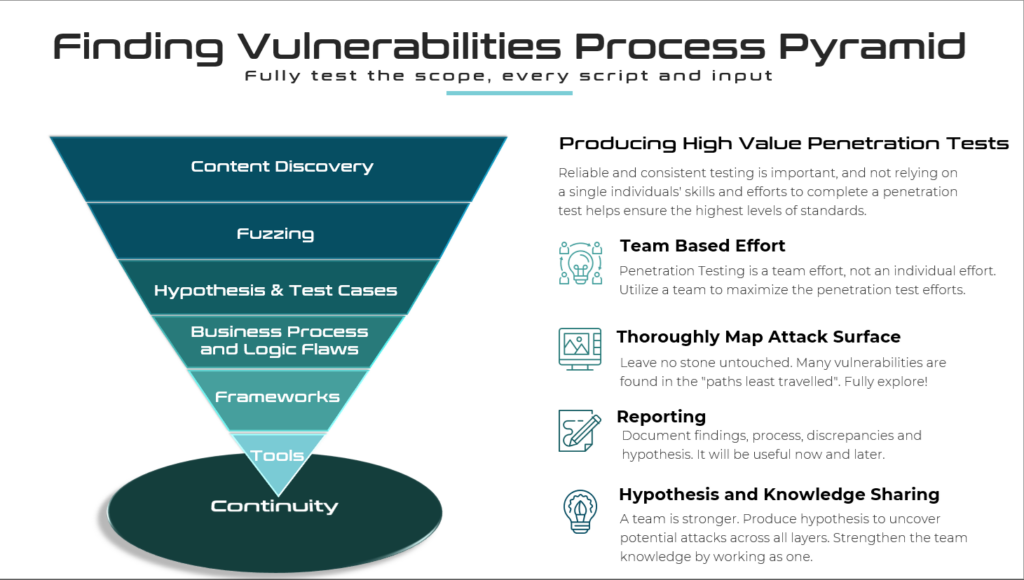
Penetration Testing Methodology – Much More Than Just Checklists
This blog post seeks to outline key aspects of the methodology River Security employs to identify vulnerabilities during our penetration testing. Our approach is continually evolving, designed to adapt to...
Finding Attack Surface and Other Interesting Domains via Certificate Transparency Logs
Certificate Transparency (CT) logs are like public records for internet security. When a new TLS certificate is issued, it gets logged in these CT logs. This makes it easier for...
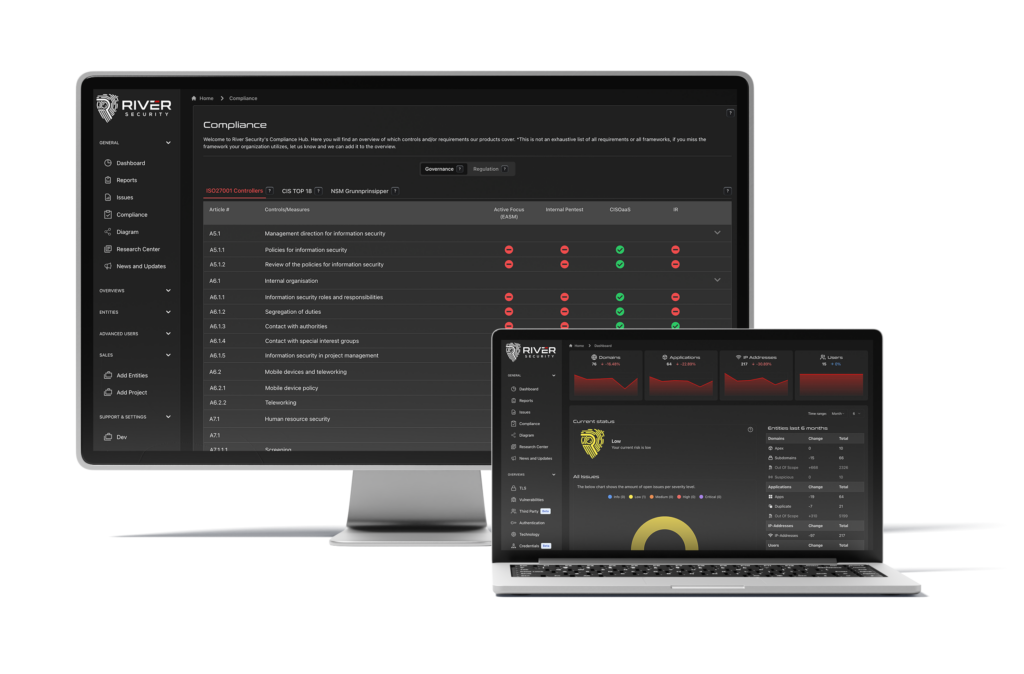
Strengthening the Fort: How Attack Surface Management Empowers Companies in Web Security, Mail Security, Credential Management, and Authentication
There are many "vulnerabilities" that don't need immediate fixing; best practices, security hygiene and many other priorities risk taking priority over other more important security factors. At River Security, we...