Why We Monitor Technology
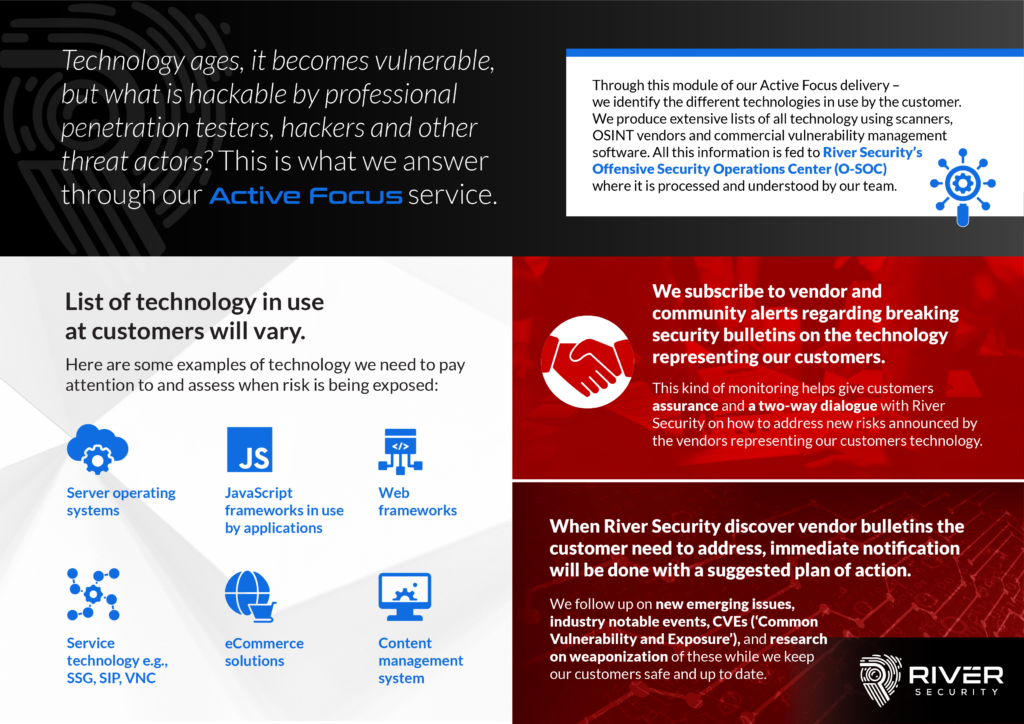
A key pillar in every organizationTECHNOLOGY Why and how do we monitor it? What kind of opportunities does it present our Offensive Security Operations Center? With aged technology comes vulnerabilities....
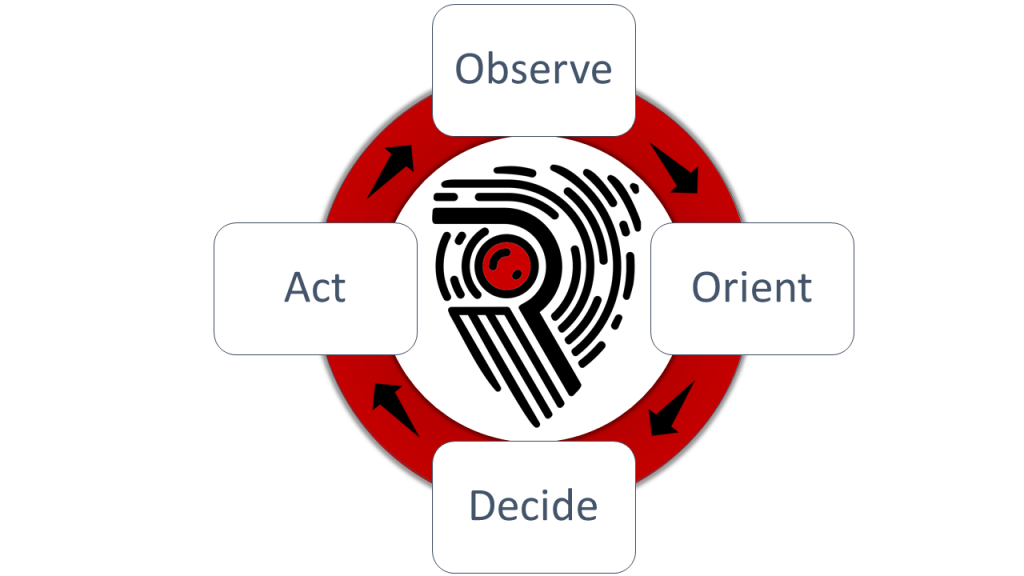
OODA Loops, Speed and Agility
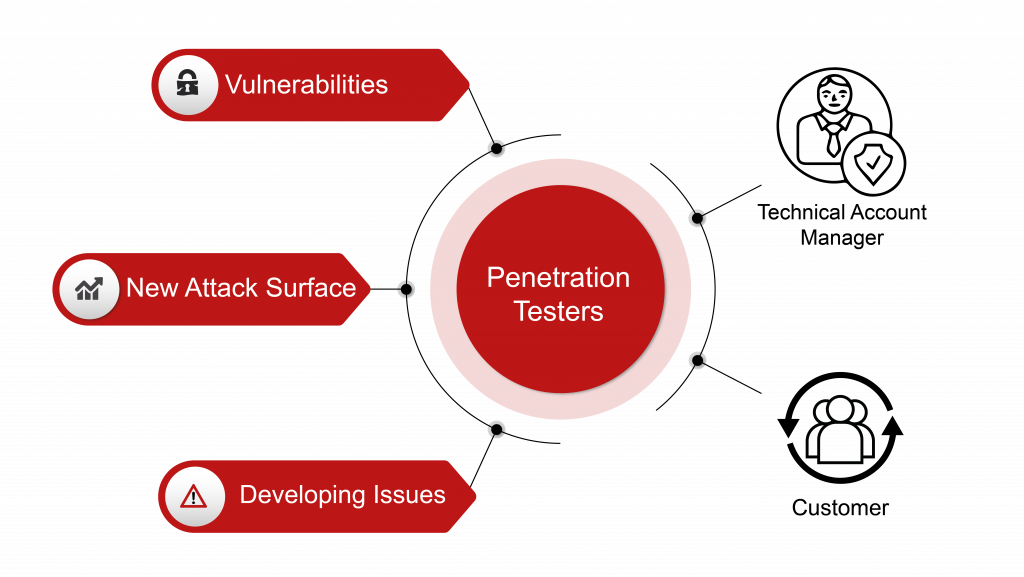
To beat attackers at their own game, it is imperative River Security is able to more rapidly detect, uncover and find flaws in our customers environments than the threat actors....
Know Your Enemy
River Security follow closely the attackers' behaviors and attack techniques. In studying attackers Tactics, Techniques and Procedures (TTP's), our tools are sharpened and tailored to discover weaknesses in organizations defenses...
Ransomware Roulette – Level up or pay up
As we all know, at least to some extent, cryptocurrency solved the main problem (if we ask threat actors, that is) in ransomware and extortion attacks – getting away with...