Community
Content
All
- All
- Attack Surface Management
- Incident Response
- News
- Penetration Testing
- River Security
Finding Attack Surface and Other Interesting Domains via Certificate Transparency Logs
Certificate Transparency (CT) logs are like public records for internet security. When a new TLS certificate is issued, it gets logged in these CT logs. This makes it easier for...
Celebrating 4 Years of River Security: A Journey of Growth, Success and Stopping the Threat Actors!
As we celebrate our fourth anniversary, we at River Security are filled with immense pride and gratitude. What started as a small, ambitious venture has now grown into a robust...
The Penetration Testers Manifesto
This is River Security's ethos—our belief system, motivation, and inspiration. Interested in working with us? Check out our jobs page. As a hacker, I am driven by a relentless curiosity...
Continuous Security, Real Risk Insights, and Business Value – Why Our Customers Choose Active Focus
A few years back, River Security developed and launched Active Focus, a world-first, disruptive IT security technology and service enabling penetration testers to be always-on, properly fighting against the adversary...
Say hi to Martin
We are happy to announce that Martin Andreassen has joined River Security as a Business Developer. Martin is an INSEAD MBA with significant international exposure, having lived and worked in...
Ethical Considerations in Incident Response
Ethical considerations in incident response, especially when dealing with sensitive data and disclosing information about security breaches, are paramount. These situations require a careful balance between transparency, confidentiality, legal obligations,...
Welcome William
We are delighted to introduce William Kristoffersen as our latest team member, stepping into the role of Senior Penetration Tester! Through thorough interview rounds and his active participation in our...
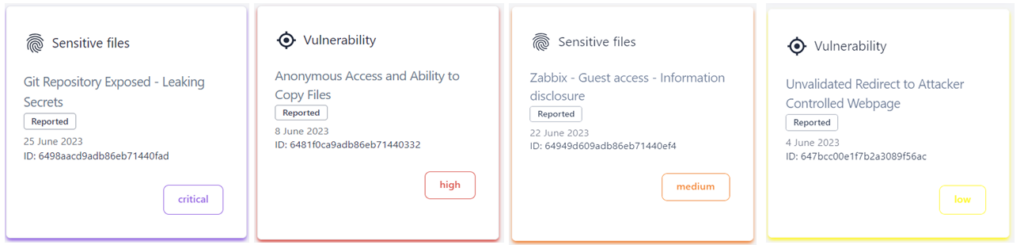
Distinguishing Vulnerabilities, Security Hygiene, and Exploitable Issues – Our Approach
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats requires a keen understanding of the nuanced differences between vulnerabilities, security hygiene, and issues with demonstrable impacts on confidentiality,...
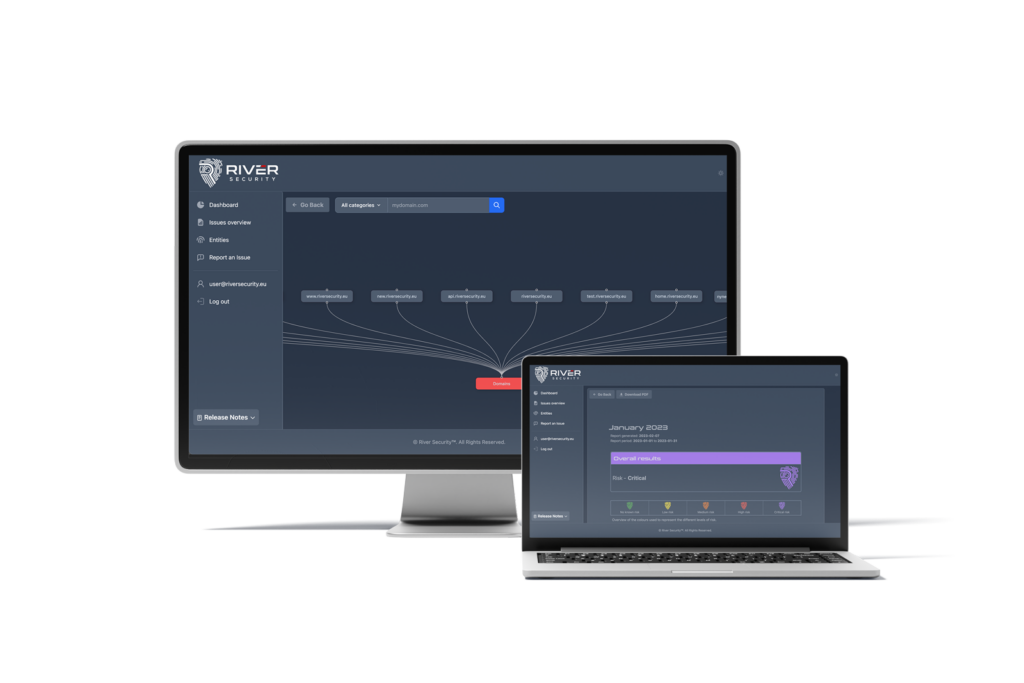
Strengthening the Fort: How Attack Surface Management Empowers Companies in Web Security, Mail Security, Credential Management, and Authentication
There are many "vulnerabilities" that don't need immediate fixing; best practices, security hygiene and many other priorities risk taking priority over other more important security factors. At River Security, we...
Beyond Bug Bounty – Elevating Security with Attack Surface Management
In an era where cybersecurity threats constantly evolve, organizations must stay ahead of malicious actors to safeguard their digital assets. Bug bounty programs have surged in popularity recently as a...