River Security
Welcoming Tomasz Czyz – Senior Penetration Tester
We are pleased to announce that Tomasz Czyz is joining River Security as a Senior Penetration Tester. Tomasz joins us from Atea, where he has worked as a Senior Security...
Turning Cloudflare Into an SSRF Engine, Reaching What You Were Never Meant to See
[Editor note: Raymond identified a potential SSRF issue within Cloudflare infrastructure. While initially difficult to exploit due to limitations and unexpected behavior, further investigation confirmed real impact. By leveraging Cloudflare’s...
Welcoming Martin Nyberg – Penetration Tester
We’re excited to welcome Martin Nyberg to River Security, who joins us as a Penetration Tester in our Offensive Security Operations Center (OSOC). Martin comes from a strong technical background...
Welcoming Valdemar Andersen – Threat Intelligence Manager
We’re excited to welcome Valdemar Andersen to River Security, who joins us today as our new Threat Intelligence Manager. Valdemar comes to us from the role of Senior Cybersecurity Consultant...
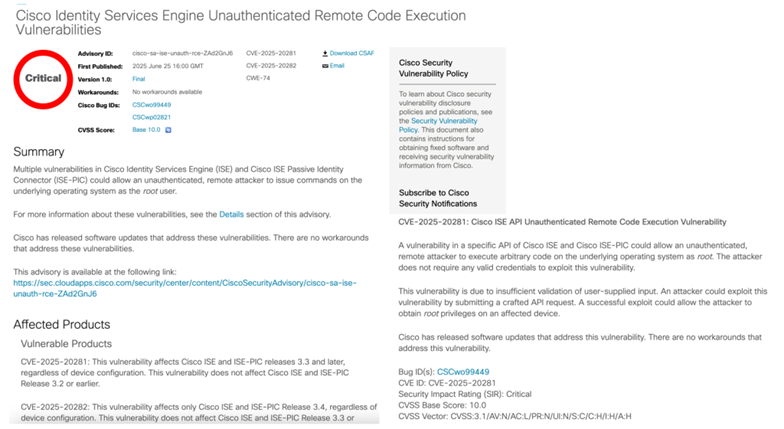
Like stealing (Cisco) ISE-cream from a kid – Weaponizing a CVE
[Editors Note: Raymond Strandheim is a principal pentester, and I asked him to share with us how he managed to weaponize a new vulnerability from Cisco into a working exploit...
From Norway to Sweden – with Europe in sight
Jens Dahlkvist (Country Manager Sweden, left) and Andreas Claesson (Principal Penetration Tester, right) With local leadership and senior expertise, we’re ready to meet the Swedish market River Security continues its...
Sikkerhetsfestivalen 2025: Reflections and the Road Ahead for Cybersecurity
Introduction What a festival. Sikkerhetsfestivalen 2025 – my first, and definitely not my last. The organizers and the city of Lillehammer brought together some of the sharpest companies and minds...
Welcoming Andreas Claesson – Principal Penetration Tester
We’re excited to welcome Andreas Claesson as our new Principal Penetration Tester at River Security. Andreas joined us on October 1st, bringing with him years of experience in offensive security...
Welcoming Mats Herman Heggelund – Penetration Tester
We’re excited to welcome Mats Herman Heggelund as our new Penetration Tester at River Security. Mats joined us in September and is already proving himself as a strong addition to...
Three Years of Building the Unbuildable
It’s been three years since I jumped head-first into building the backend systems behind River Security’s ActiveFocus platform, the engine our penetration testers rely on to continuously identify, surface, and...