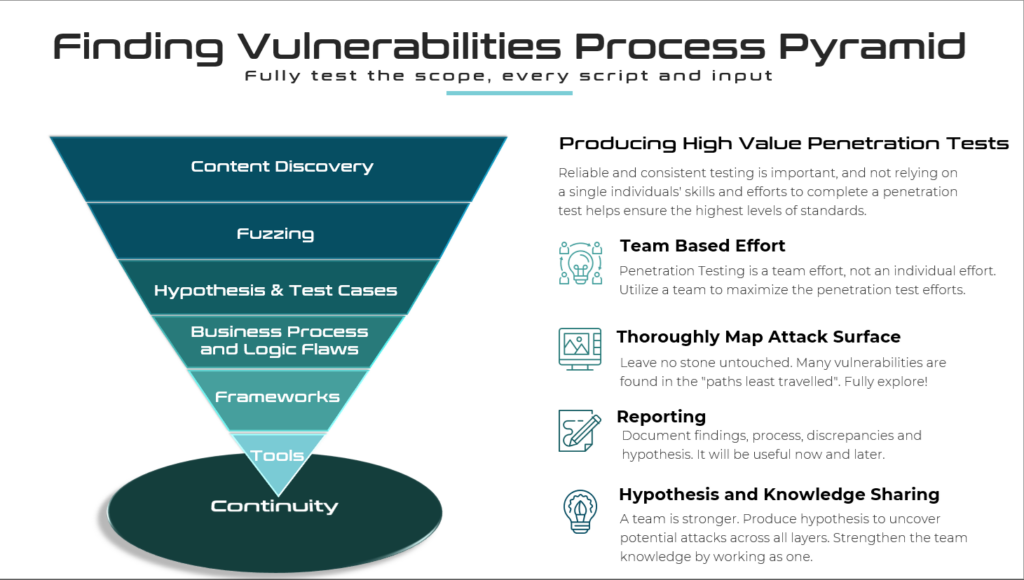
Penetration Testing Methodology – Much More Than Just Checklists
This blog post seeks to outline key aspects of the methodology River Security employs to identify vulnerabilities during our penetration testing. Our approach is continually evolving, designed to adapt to...
Finding Attack Surface and Other Interesting Domains via Certificate Transparency Logs
Certificate Transparency (CT) logs are like public records for internet security. When a new TLS certificate is issued, it gets logged in these CT logs. This makes it easier for...
The Penetration Testers Manifesto
This is River Security's ethos—our belief system, motivation, and inspiration. Interested in working with us? Check out our jobs page. As a hacker, I am driven by a relentless curiosity...