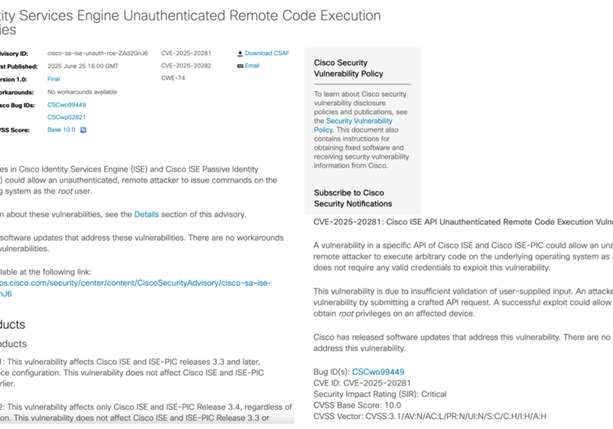
Finding Attack Surface and Other Interesting Domains via Certificate Transparency Logs
Certificate Transparency (CT) logs are like public records for internet security. When a new TLS certificate is issued, it gets logged in these CT logs. This makes it easier for us to track and monitor all certificates tied to our customers domains, and perhaps more importantely, their brands. By regularly checking these logs, and subscribing to the logs via real-time updates, we can spot new attack surface early in its life cycle, and any unauthorized certificates that might have been issued for our domains. This is crucial because such certificates can be used by attackers to launch phishing attacks or spoof our brands.
CT logs in other words also help us find fraudulent domains. Cybercriminals often create fake domains that look like real ones to trick users. By analyzing CT logs, we can identify these suspicious domains early. For example, we can spot domains that have slight spelling changes or use similar-looking characters to mimic trusted sites. Catching these fraudulent domains quickly allows us to take action before they can cause any harm. In short, CT logs are a valuable tool in our cybersecurity toolkit, helping us protect our domains and users from potential threats.
Using Active Focus our team of penetration testers has managed to compromise a targets ridicoulusly fast via the following methodology:
- Monitor certificate transparency logs to identify any instances of your target brand name.
- When a new certificate is detected, perform DNS delta checking to determine if the domain resolves to an IP address.
- If the domain resolves to an IP address, initiate regular port scans to discover available network services.
- Once network services are identified, conduct assessments with penetration testers. Additionally, employ delta checking to monitor for changes and new deployments.
- When there is a change, proceed with your security testing and exploitation as needed.
Certificate Transparency for Penetration Testers, Bug Bount Hunters and Threat Actors
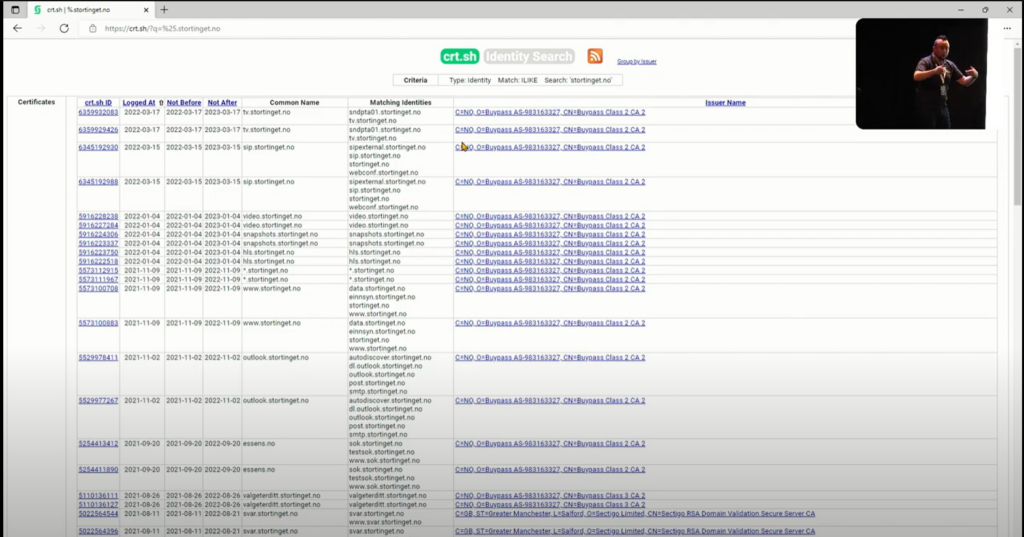
As we’ve mentioned earlier, Certificate Transparency (CT) logs can sometimes enable our penetration testing team to highlight risks to our customers with astonishing speed. Often, our clients are amazed at how quickly we can identify vulnerabilities and demonstrate their security gaps. Are you curious about what CT logs can reveal about your domain? Fortunately, tools like crt.sh allow you to search the historical issuance of certificates for any given domain. For example, you can search for %.sans.org to find all certificates issued for sans.org and its subdomains.
Even if real-time monitoring of CT logs is not feasible for you, you can still search through them to uncover potential attack surfaces quickly. Crt.sh also supports direct querying via SQL, allowing penetration testers and bug bounty hunters to search the database from the command line, providing a powerful tool for comprehensive security assessments.
Finding vulnerabilities often require you to have first movers advantage, and hopefully we have been able to demonstrate to you how CT logs can help in achieving that.
Why do we have CT logs?
Considering that CT logs pose a possible blatant information leak if you are not aware of them, it is quite natural to ask ourselves, why do we even have them? Certificate Transparency (CT) logs were introduced to address weaknesses in the certificate issuance system. Before CT logs, it was difficult to detect misissued or malicious certificates because there was no public record of issued certificates. CT logs solve this by creating a publicly accessible repository of all issued certificates. This allows anyone to monitor and audit the issuance of certificates, making it easier to detect and respond to unauthorized or fraudulent certificates, enhancing overall internet security by ensuring transparency and accountability in the certificate issuance process.
Meta has a service where they can notify you when a new certificate has been created: https://developers.facebook.com/tools/ct/search/, while Cloudflare has a similar notification system: https://developers.cloudflare.com/ssl/edge-certificates/additional-options/certificate-transparency-monitoring/.
Even your browsers can implement Certificate Transparency as a security measure, for example Google Chrome. Google Chrome has been a pioneer in implementing CT. Since May 2018, Chrome requires all publicly trusted TLS certificates to be logged in CT logs to be recognized as valid. This means that if a certificate is not logged, Chrome will not trust it, thereby preventing users from accessing the site. Chrome also introduced the Expect-CT header, which allows site operators to instruct browsers to only trust certificates logged in CT logs.