OODA Loops, Speed and Agility
To beat attackers at their own game, it is imperative River Security is able to more rapidly detect, uncover and find flaws in our customers environments than the threat actors. This process boils down to a process known as a OODA Loop.

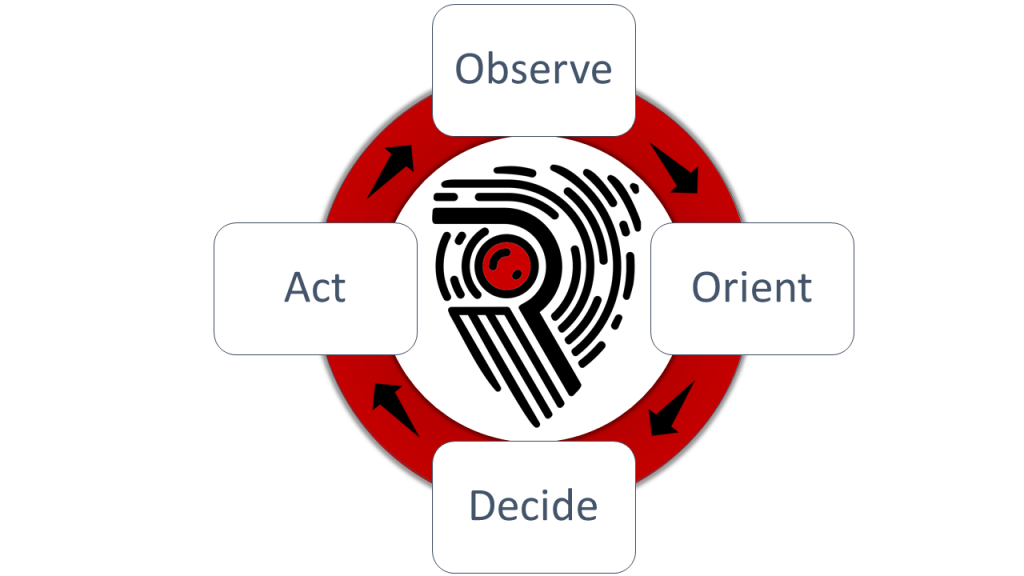
The OODA loops is a concept we have borrowed from the military. It helps us achieve speed and agility within our processes. Our agile processes and team help us to rapidly:
- Observe changes and developing threats in our customers landscape
- Orient ourselves and the customer on the matters at hand
- Decide which measures to defeat the adversary with
- Act on the measures
By focusing our own OODA loops and making them faster than our adversaries will help us win the fight.
Speed – How We Become Lightning Fast
Speed matters, and the faster and sooner we can bring our customers the latest news about what is going, the sooner we can start making ourselves secure. River Security makes many reports every month on our latest recommendations in protecting our customers infrastructure. These recommendations helps our clients continuously prioritize in an IT landscape which is ever changing.
Integrations into our customers environments ensures that our alerts and notifications hit our customers in their existing pipelines, allowing us direct correspondence with the teams responsible for fixing the issue.
To ensure speed and focus from the right team on the right issues, our team writes scripts and solutions to help find changes in our customers infrastructure.
Agility – Micro Prioritizations Every Day
The security industry has for years been lagging behind on common practices within agile development, design and processes. By taking lessons from agile processes, our organization is now faster, smarter and more responsive. This enables us to focus on micro-tasks and continuous refocus of prioritization, instead of heavy and hard to change projects.
By driving agility within our penetration testing and Attack Surface Management processes, our team is capable of working together on missions, instead of the common problem of prioritizing every task on one resource. This comes especially in handy when threats are developing, new attack surface is discovered and other notable events.
What We Monitor – Cyber Security Is Not One-Size Fits All
Cyber Security is not a one-size fits all and the teams at River Security loves this! It would be unfair to our customers to limit ourselves in monitor just one or a few threats and techniques, and it would not work. Cyber Security changes rapidly, and so does River Security. We constantly seek new ways of getting a hold of interesting data sets, new tools to find vulnerabilities and other ways to support our customers the best. This all happens based on the developing threats and changes to the industry.
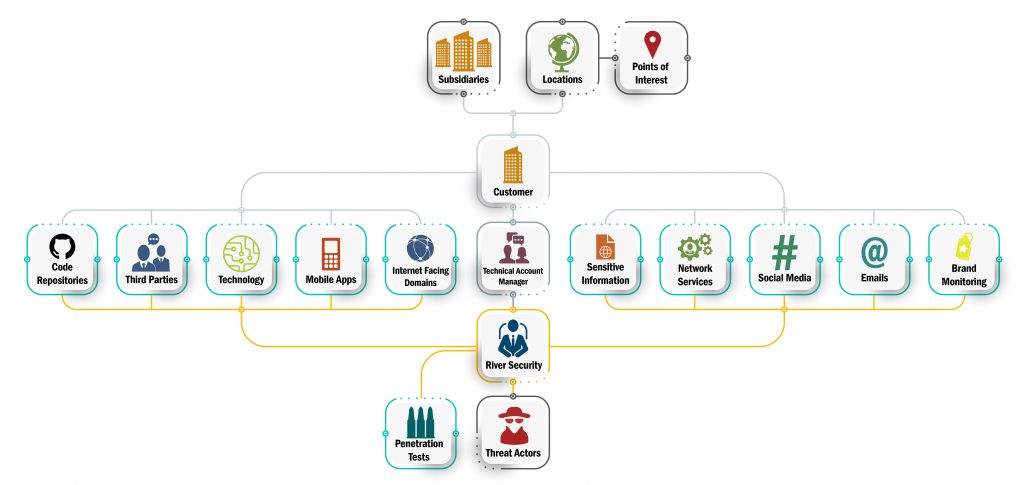
While many solutions try to appeal to the mass market, solutions which are perhaps generic enough to fit every customer, we are instead always developing new components based on what our customers have. The image below shows the high level architecture for our customer deployments.
Read more about what we monitor in our post on “Know Your Enemy”.