Active Focus is a continuous, proactive defense service that fundamentally changes how developers and Operation teams manage security risks in an agile day.
We combine four foundational pillars:
-
Continuous Attack Surface Management (ASM) maps and tracks every externally visible asset (domains, APIs, services) in real time, so changes don’t go unnoticed.
-
Continuous Penetration Testing, not periodic point-in-time pentests, but always-on offensive discovery and testing whenever the attack surface changes.
-
Offensive Security Operations Centre (Offensive SOC) with human expertise validating and prioritising findings, not just raw machine scans.
-
Threat Intelligence and prioritized actionable insights rather than noise and generic vulnerability lists.
“We created the customer portal so you can learn who you are and what you need to defend.”
- Herman, Platform Development Engineer
Why It Matters for Dev/Ops teams

Aligning with Modern DevOps Velocity
Traditional security checks (quarterly scans, annual pentests) do not match the cadence of changes in CI/CD pipelines, cloud infrastructure, microservices, third-party APIs, and ephemeral workloads. Continuous attack surface discovery and testing ensure every new deployment or configuration change is assessed without slowing teams down.
Bridges Security and Engineering Mindsets
Dev/Sec/Ops is about integrating security into development and operations, not siloing it. Active Focus provides continuous, context-rich insights, enabling developers and operators to see what an attacker sees of real, exploitable weaknesses. Not just a laundry list of potential issues.
Actionable, Prioritised Findings Over Noise
Most automated scanners produce thousands of low-value alerts. Active Focus adds expert validation and prioritisation, enabling teams to focus on what actually matters and understand the risk impact.
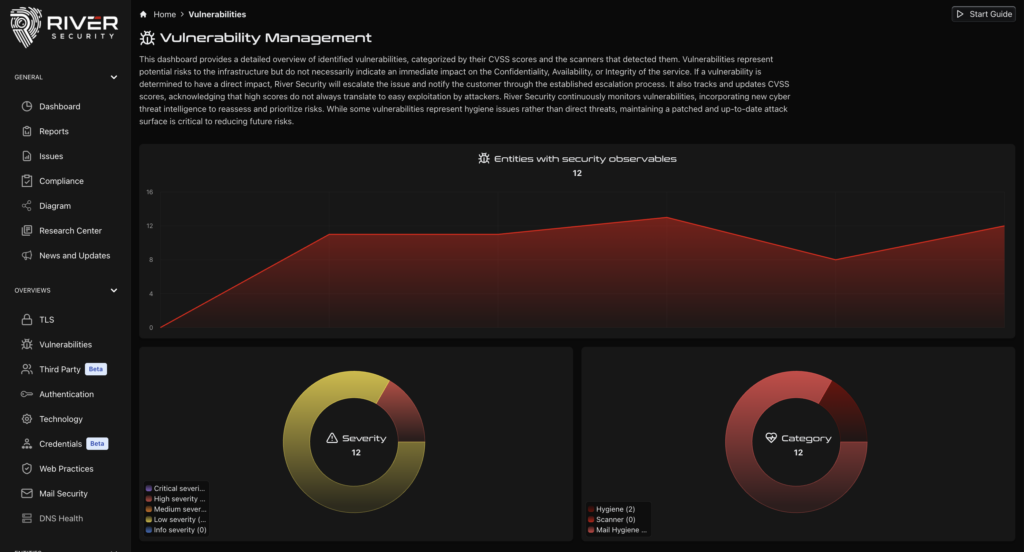
Proactive vs Reactive Security
Dev/Sec/Ops thrives on feedback loops. Active Focus continuously tests changes as they happen, rather than waiting for scheduled assessments, enabling rapid remediation and reducing exposure windows.
Security That Scales With Infrastructure Complexity
As organisations adopt cloud, containers, serverless, and microservices, static assessments don’t scale. Continuous monitoring adapts to dynamic environments, ensuring risk visibility remains current.
Supporting Automation and Integration
The River Security customer portal and APIs give teams programmable access to continuous security data so they can integrate findings directly into dashboards, ticketing systems, or automated workflows—crucial for true Dev/Sec/Ops practices.
Compliance Hub
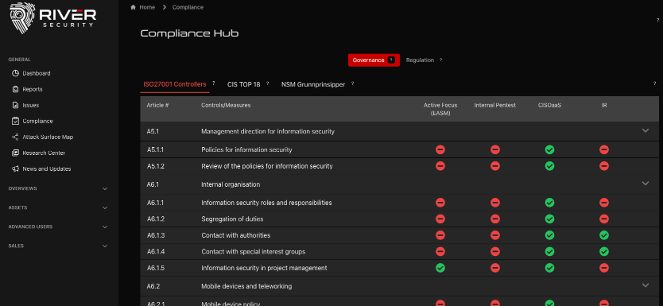
Compliance and Risk Context
Continuous testing and exposure visibility support frameworks like NIS2, DORA and ISO standards by providing ongoing evidence of risk assessment and mitigation. This harmonises operational security work with compliance requirements.
Trusted by
“River Security did a penetration test and assessment of the cyber security of our product. The team at River did a great job in understanding our systems in no time. They were highly efficient in analyzing every piece of our solution, both on our physical devices and on our cloud systems, and gave continuous feedback to us on things to improve.”
“As part of our ongoing security efforts, we’ve engaged external experts, River Security, to assess our security posture. They specialize in offensive security, or “Red Team” activities, and we affectionately refer to them as “kind bandits.”
“InfoTiles chose to work with River Security for our most recent penetration testing, because Vegard quickly understood our objectives and delivered a work plan that complements the agility critical to scaling companies.”
“At Lisa Solutions, ensuring the security of our software and protecting our customers’ data are top priorities. We are pleased to share that River Security recently conducted a penetration test, which confirmed the strength and resilience of our systems.”
“…That’s where River Security comes in, offering their Active Focus service to keep us ahead of the curve with a constantly evolving attack surface, and even helping us to uncover the unknown…”
“The team is very knowledgeable and has taught us a lot when it comes to proactive cyber security. They are agile and clearly has a lot of competence within their field, and we are happy to have them on our side in the ever-changing threat landscape.”
“One of the differentiating features of River Security is that they focus on real threats and areas that need attention – so we not only know about vulnerabilities, dark web disclosures and other issues, but also how they will affect our business.”
“River Security conducted a Digital Footprint and an internal Penetration Test on our systems. Our experience with the team from River Security shows that they are highly skilled professionals. Throughout the project we really appreciated their enthusiasm and great interaction with our own team.”
“As the uncertainty surrounding the situation in Europe continues, security in critical infrastructure is of higher importance than ever. Having an external party look at your company from an attackers’ point of view is crucial to identify weaknesses, but also to confirm good measures already in place.”
“We had the pleasure of hosting a Secure Coding Session for our developers, led by Chief Hacking Officer Chris Dale from River Security AS. The workshop from River Security was tailored to our development team and provided valuable insights into best practices for writing robust and secure code. “










