Insights from a Hacker's Perspective
Uncover invaluable perspectives by gaining insights from a hackers viewpoint. Discover vulnerabilities and potential entry points in your digital infrastructure, enabling you to fortify your defenses and stay one step ahead of cyber threats.
Map Your Attack Surface
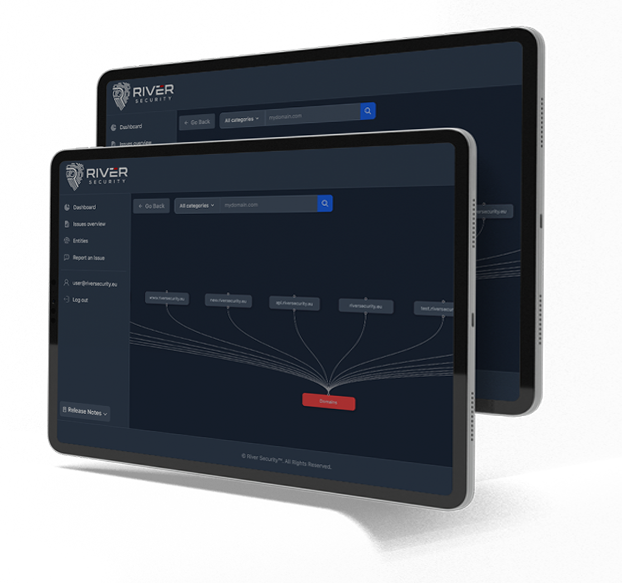
Visualize and comprehend the entirety of your attack surface through our detailed mapping, the fundation of Attack Surface Management (ASM). Identify potential risks, vulnerabilities and weak points across your digital landscape, empowering you to implement targeted security measures for comprehensive protection.
Reports Curated by Experts
Receive meticulously crafted reports curated by our team of experts. Benefit from concise, actionable information about vulnerabilities, risks and recommended security measures tailored specifically to your organization's digital footprint.
Remediate What Matters
Leverage the expertise of our seasoned professionals to receive strategic guidance on prioritizing your security efforts. Gain insights on identifying critical areas that require immediate attention, enabling you to allocate resources effectively and proactively address the most high-risk vulnerabilities first.
Advantages of Knowing Yourself - Your Digital Footprint
Mapping out your digital footprint should be a key priority for all companies before undergoing a penetration test, to identify vulnerabilities. This activity provides many advantages, including significant cost savings and faster results. By gaining a clear understanding of their digital assets, organizations can quickly identify any weaknesses or systems that require maintenance before undergoing a penetration test. This ensures that the penetration test provides the most valuable feedback, focusing on what matters most to your organization.
How does it work?
Engaging with the River Security team initiates a focus time period during which we conduct a thorough examination of your digital presence across the internet. Our meticulous search aims to identify all assets and their corresponding risks to provide you with comprehensive insights.
Our Digital Footprint serves as a crucial starting point for understanding the exposure, risks, and attractiveness of your assets to potential attackers. By carefully assessing the significance of potential targets, we enable you to implement robust security controls and ensure proper protection.
Rest assured, our Digital Footprint activities are designed to be harmless to your company assets. We prioritize the utmost care and professionalism to deliver insightful results without posing any risk to your organization's infrastructure.
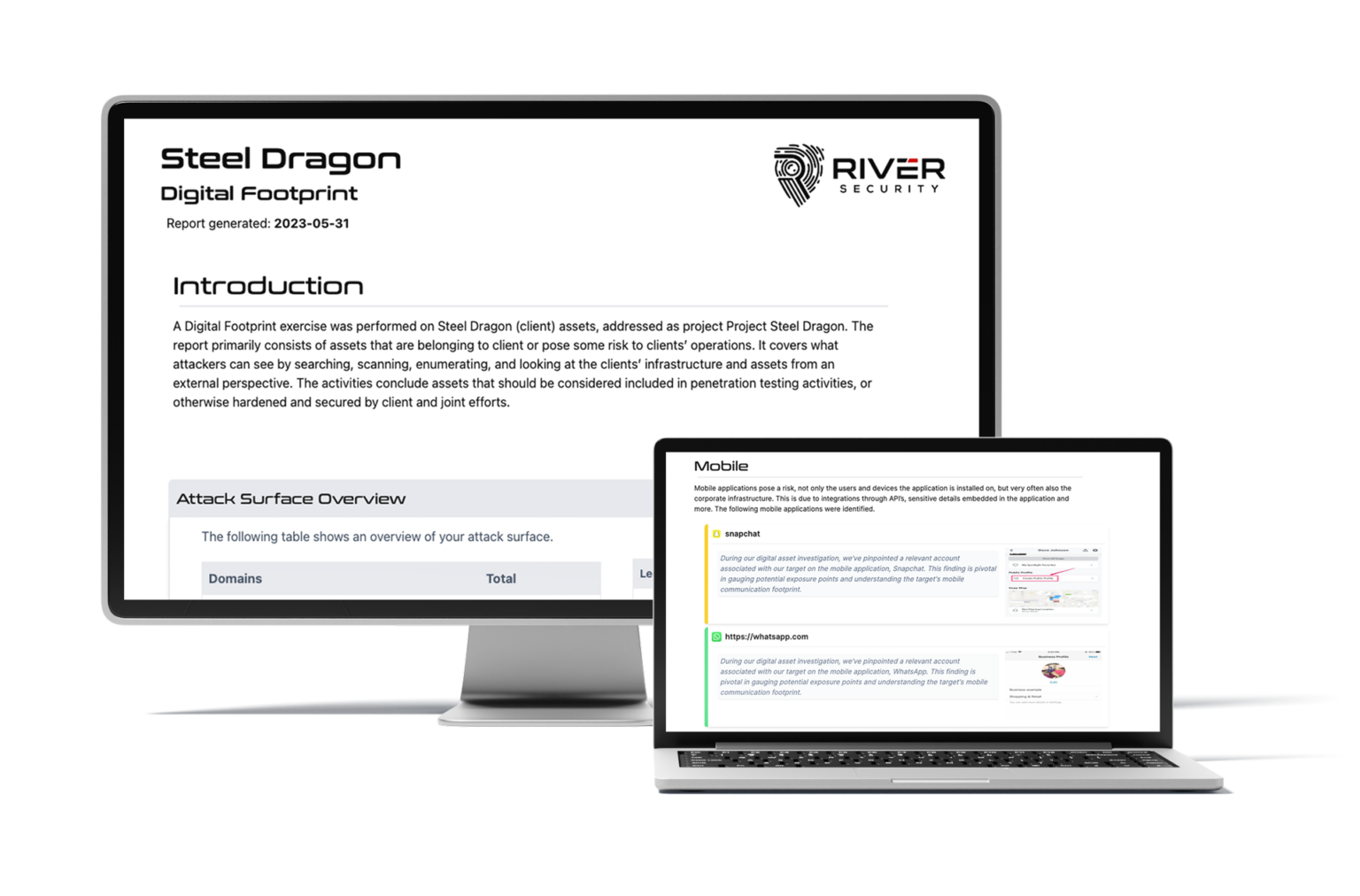
The Report
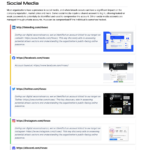
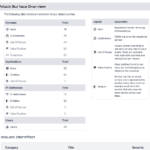
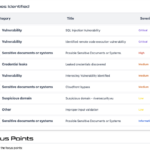
Our discovery and assessment of all the assets will be included in a report. The report covers everything we have been able to observe our customer have in terms of digital assets.
The report typically gives immediate value to our customer. Within the report we will find focus areas revealing anything from credentials which must be changed, abandoned or unmaintained systems, old and vulnerable systems and more.
The report lists assets based on our penetration testers priorities. Systems we prioritize highly are those which expose risk and at the same time has a high value for our customer. For example an outdated VPN service providing access to internal networks would be a critical target for our customer to address, especially before criminals leverage the VPN to install malware such as ransomware.
Click to see some content from an example report.
Steps to better security hygiene
Our Customers Say It The Best



The team is very knowledgeable and has taught us a lot when it comes to proactive cyber security. They are agile and clearly has a lot of competence within their field, and we are happy to have them on our side in the ever-changing threat landscape.

Terje Einar Hunvik
Mesta
One of the differentiating features of River Security is that they focus on real threats and areas that need attention – so we not only know about vulnerabilities, dark web disclosures and other issues, but also how they will affect our business.

Ole-Martin Bækkeli
Azets
...That’s where River Security comes in, offering their Active Focus service to keep us ahead of the curve with a constantly evolving attack surface, and even helping us to uncover the unknown...

Arvid Eriksen
Sparebanken Vest
More about our service in these selected articles
Continuous Penetration Testing: Why Fresh Eyes Find Fresh Bugs
[Editor’s note: I wrote this short blog post to illustrate the advantages of Continuous Penetration Testing. In this case, a tester discovered a vulnerability triggered by a new event in Active Focus, even though the same issue had been missed during a previous test. It’s a great example of why continuous testing matters. ~Chris Dale]…
SSL/TLS Management: Reducing Risks and Gaining Visibility
Transport Layer Security (TLS) and its predecessor SSL remain cornerstones of modern internet security. They protect confidentiality, integrity, and authentication for data in transit. But while TLS is everywhere, managing it across an organization’s infrastructure is far from straightforward. Poor management introduces hidden risks that attackers are quick to exploit. Why TLS Management Matters For…
Pentesting is Transforming: 8 Steps to a Successful Pentest Operation in 2025!
Pentesting isn’t what it used to be, folks. Gone are the days of single checklist exercises and surface-level scans. In 2025, we’re transforming the way we think about pentesting—making it a dynamic, intelligence-driven, and collaborative practice that does more than just “find vulnerabilities.” We’re taking a proactive, adversary-informed approach that considers not only what’s in…