Offensive validation matters
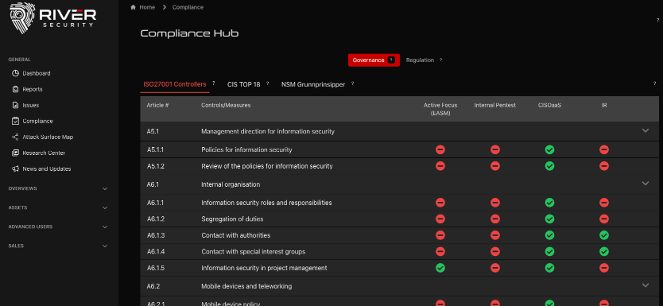
Energy operators do not benefit from long vulnerability lists or unvalidated scanner output. What matters is whether a weakness can actually be exploited and which concrete operations it could lead to. For the energy sector, this is especially important because:
- OT vulnerabilities often require context to assess real impact.
- False positives create unnecessary operational disruption.
- Security teams must focus on high impact, low tolerance risks.
“Active Focus combines continuous attack surface monitoring with offensive security validation by human experts. This ensures findings reflect real attacker behavior, not generic theoretical risk.”
- Jan Petter, Threat Intel Manager
Protect high value assets in a high risk environment
Energy companies operate some of the most critical infrastructure in society. The combination of legacy systems, modern cloud platforms, third party integrations, and increasing IT OT convergence creates a uniquely exposed attack surface. In this sector, even small technical weaknesses can have disproportionate operational, safety, regulatory, and reputational consequences. Active Focus directly addresses this reality by providing continuous visibility into what is exposed, how it changes, and what can actually be exploited, rather than relying on periodic assessments that leave long windows of unknown risk. Our solutions are trusted by:
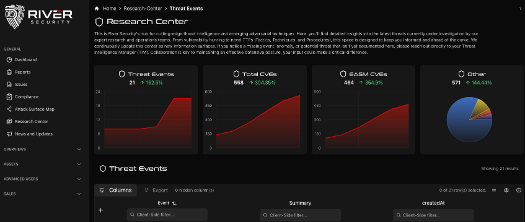
Continuous visibility where periodic security fails
Energy environments change constantly. New remote access solutions, vendors, monitoring platforms, and integrations are introduced to keep operations efficient. At the same time, many OT systems were never designed to be internet facing.
Active Focus continuously maps the external attack surface, including internet facing IT and OT assets. This is critical because River Security has repeatedly identified exposed OT systems and unintended internet exposure that organisations were unaware of. These are not theoretical risks. They are real, reachable systems with real world impact.
For energy companies, this means:
-
Exposures are identified as they appear, not months later
-
Shadow assets and forgotten systems are discovered
-
Misconfigurations are caught before they are exploited
For leadership this reduces uncertainty and strengthens the ability to demonstrate due diligence when incidents occur.