Continuous Penetration Testing That Drives Measurable Impact
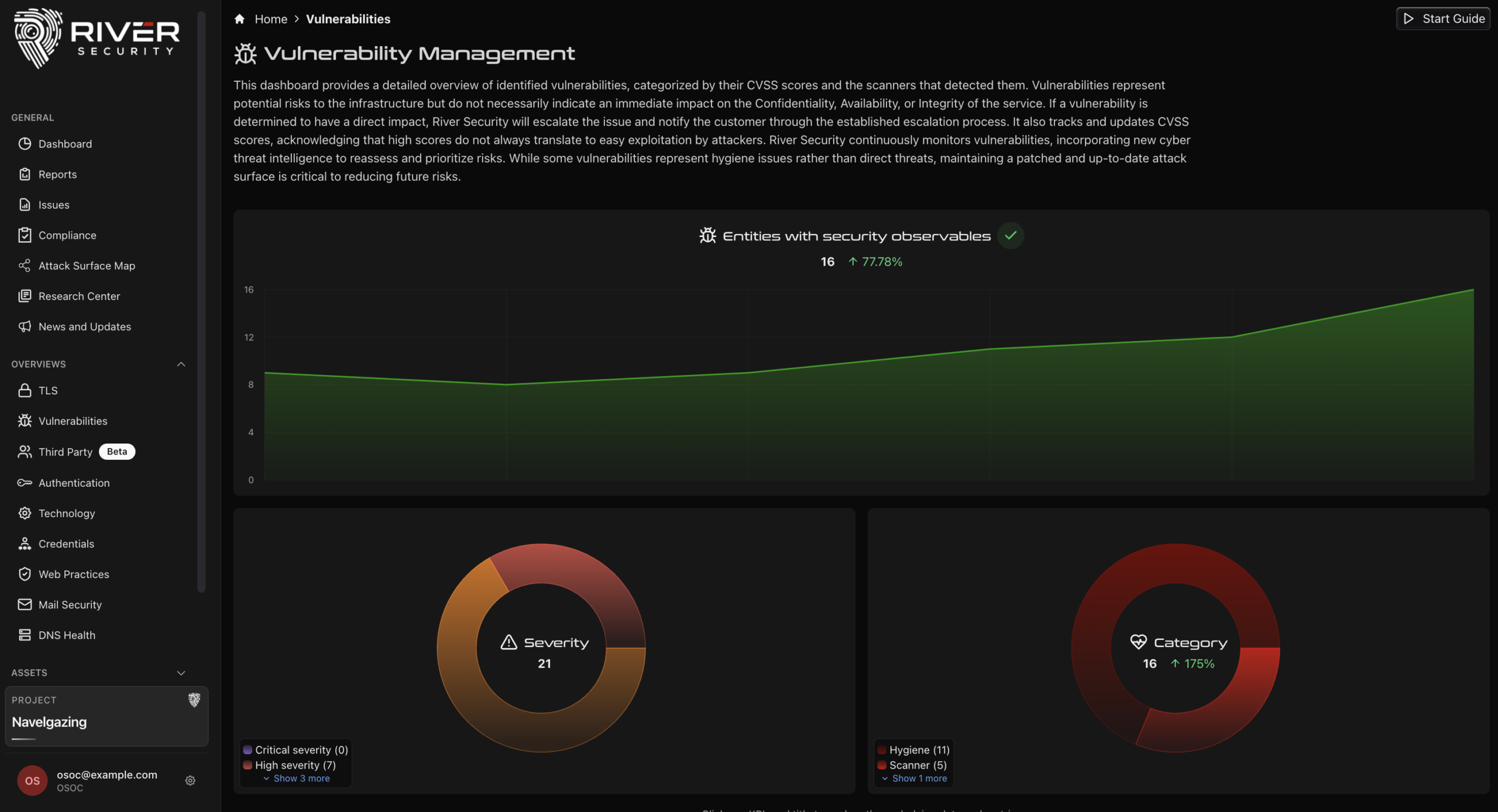
Traditional penetration testing has a fundamental problem: it is a snapshot of your security posture on one specific day. By the time you receive the report, new code has shipped, infrastructure has changed, and your attack surface has evolved. Active Focus fundamentally challenges this outdated model with continuous, real-time penetration testing that identifies and prioritizes vulnerabilities as they emerge, not months later.
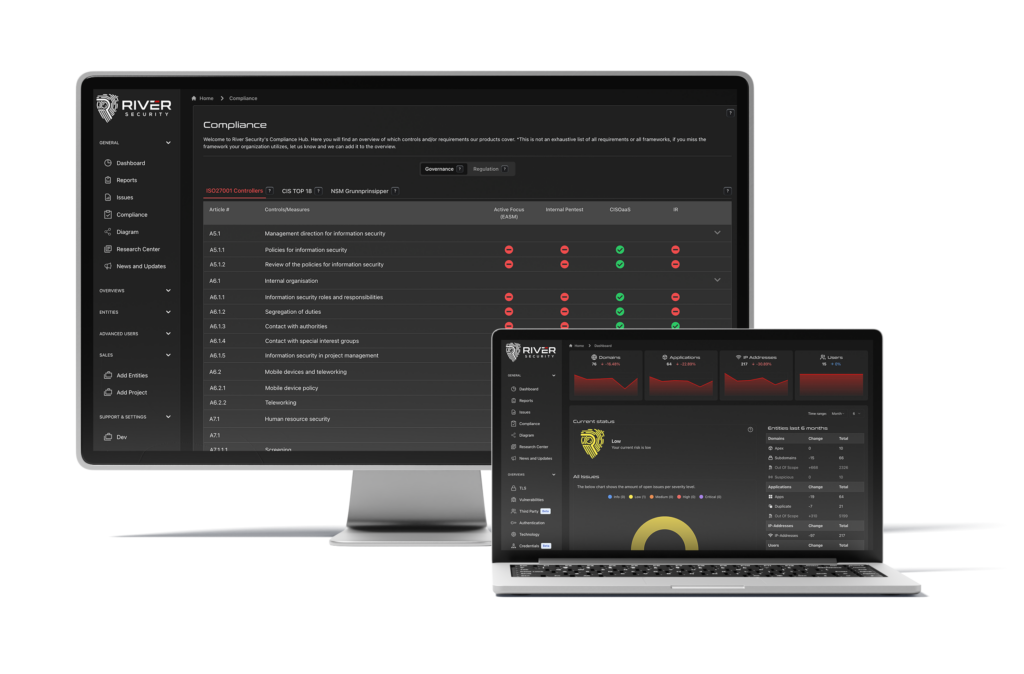
Beyond Compliance Checkboxes
Meeting regulatory requirements like NIS-2, DORA, and CIS-18 is more than ticking boxes on an annual audit. Active Focus provides the continuous security validation these frameworks actually demand. Our platform automatically maps your security controls against compliance requirements, demonstrating not just that you performed a pentest, but that you maintain an always-on, proactive security posture. When auditors come for their review, you'll have comprehensive documentation showing continuous monitoring, rapid remediation, and a mature security program that goes far beyond minimum compliance.
From our customers
“River Security has helped us turn external exposure into clear priorities. The combination of continuous testing and practical…
“With Active Focus, we can work proactively instead of reactively. Vulnerabilities are identified early, before they become an…
“River Security did a penetration test and assessment of the cyber security of our product. The team at River did a great job in understanding our systems in no time. They were highly efficient in analyzing every piece of our solution, both on our physical devices and on our cloud systems, and gave continuous feedback to us on things to improve.”