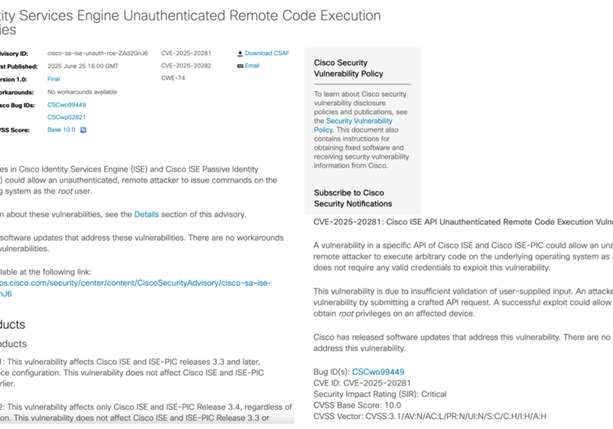
SSL/TLS Management: Reducing Risks and Gaining Visibility
Transport Layer Security (TLS) and its predecessor SSL remain cornerstones of modern internet security. They protect confidentiality, integrity, and authentication for data in transit. But while TLS is everywhere, managing it across an organization’s infrastructure is far from straightforward. Poor management introduces hidden risks that attackers are quick to exploit.
Why TLS Management Matters
For many organizations, TLS is not just about turning on HTTPS. Each endpoint, certificate, and supported protocol version represents both a control and a potential risk. Without a clear inventory and management process, security teams are often surprised by:
Certificate mismatches: When the certificate presented by a server does not align with the hostname or expected identity, users see browser warnings, and attackers may take advantage of the confusion.
Self-signed certificates: While useful in internal testing, self-signed certs bypass the chain of trust and often indicate weak validation or forgotten systems.
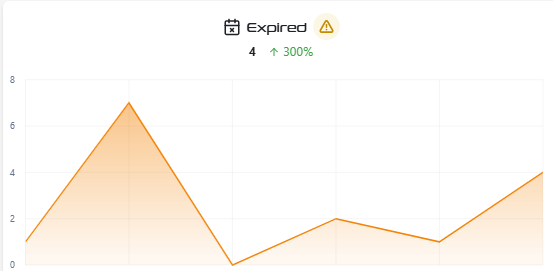
Expired certificates: Few things cause outages as predictably as an expired TLS certificate. They break business-critical services and erode trust.
Outdated protocol versions: SSL, TLS 1.0, and TLS 1.1 are long deprecated. Even TLS 1.2 requires careful configuration to remain strong. Yet many systems still support weak cipher suites for compatibility.
Understanding Certificate Authorities (CAs) in Use
Visibility into which Certificate Authorities are trusted across your systems is critical. Organizations often discover:
- Multiple CAs being used inconsistently, sometimes because different teams or vendors issued their own certificates.
- Certificates issued by lesser-known or deprecated CAs, which may no longer be considered secure or compliant.
- Shadow IT spinning up services with certificates outside of corporate policy.
A mature TLS management process should map out which CAs are in use, where they are deployed, and whether they align with organizational trust policies.
Building an Effective TLS Management Program
Managing SSL/TLS effectively requires a balance of visibility, automation, and enforcement:
- Inventory TLS Systems
- Map all endpoints that expose TLS, including internet-facing and internal services.
- Identify services that may be hidden but still impact security posture.
- Monitor Certificate Health
- Track validity periods and receive alerts before certificates expire.
- Identify mismatches and unauthorized self-signed certificates.
- Assess Protocols and Cipher Suites
- Enforce minimum TLS versions across the environment.
- Regularly scan for weak ciphers and disable them.
- Standardize on Approved CAs
- Define trusted CAs for the organization.
- Audit certificates to ensure compliance with the approved list.
- Automate Renewal and Deployment
- Use certificate management platforms or ACME protocols (e.g., Let’s Encrypt) to avoid manual renewal errors.
- Integrate certificate issuance into CI/CD pipelines for development and production.
The Payoff of Strong TLS Management
When TLS is managed well, the organization gains more than just reduced risk:
- Fewer outages from expired certificates.
- Stronger customer trust through consistent and valid encryption.
- Compliance with industry standards like PCI DSS, HIPAA, or ISO.
- Faster response times during incident handling, since visibility into cryptographic assets is already in place.
Conclusion
TLS is one of the most critical building blocks of online security, yet it is often managed as an afterthought. By treating SSL/TLS management as a strategic security control, organizations can reduce risk, improve resilience, and maintain trust in a world where encryption is non-negotiable. Active Focus helps with this today via our online platform.